Investigation: Shadow Cyberwar, Mapping the True Scale of Israel-Iran Sabotage Operations
The shadow conflict between Israel and Iran in cyberspace reveals vital infrastructure sabotage, covert operations, and real impact on global security.
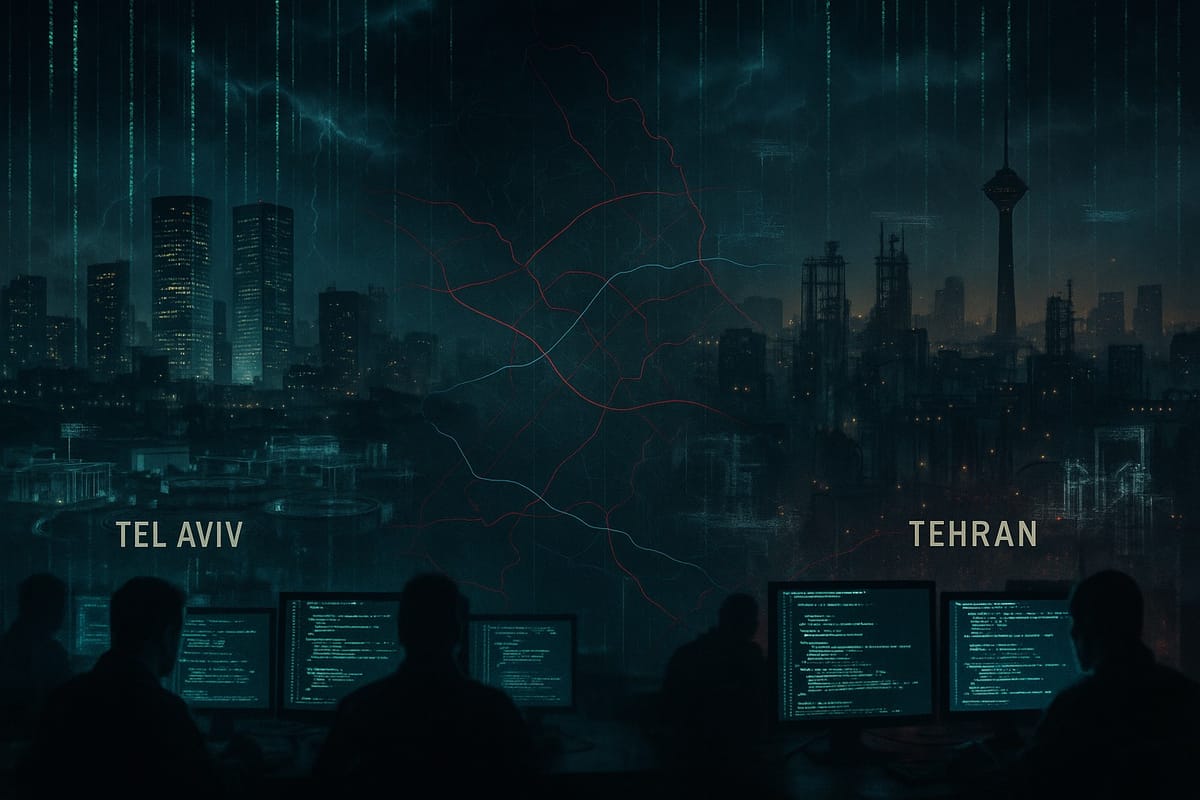
For over a decade, Israel and Iran have been locked in a shadow war in cyberspace, exchanging covert blows that often remain hidden from the public eye. This clandestine conflict has seen Israel – widely regarded as a top-tier cyber power – repeatedly deploy sophisticated malware and hacking campaigns to sabotage Iran’s critical infrastructure, spy on its sensitive programs, and even assist in high-profile missions like the assassinations of nuclear scientists. Iran, in turn, has expanded its own cyber arsenal, conducting bold offensives against Israeli targets and others, sometimes through proxy hackers or deniable operations. Crucially, many of these incidents never make global headlines. They are cloaked in secrecy, with neither side openly claiming responsibility, yet expert analyses, leaks, and cyber forensics have gradually shed light on the true scale of this hidden cyberwar.
This report investigates the full scope of the Israel-Iran cyber confrontation – beyond the famous cases like Stuxnet or the Natanz blackout – to map the frequency of attacks, the evolving tactics of their elite cyber units, the infiltration of critical infrastructure, the role of third-party actors, and the impact on civilians and global stability. We draw on open-source intelligence: cybersecurity firm reports, leaked documents, academic studies, and media investigations. What emerges is a portrait of a persistent, multi-dimensional cyber conflict that is escalating in stealth. The findings carry important implications for international norms and for any nation caught in the crossfire of state-sponsored cyber sabotage.
A Decade of Covert Cyber Attacks: Scale, Frequency, and Hidden Incidents
Waves of attacks, large and small, have struck between Iran and Israel with alarming regularity over the past ten years. While a few operations drew international attention – for example, the Stuxnet virus that crippled Iran’s uranium centrifuges in 2010, or the 2020 explosion and blackout at Iran’s Natanz nuclear facility – many others remained unpublicized or were only confirmed much later. By compiling media reports, cybersecurity analyses, and official hints, we can chart a timeline of this shadow cyberwar that reveals near-constant sparring:
- 2010 – 2012: The Opening Salvos: In 2010, the world witnessed the first truly destructive cyber weapon: Stuxnet, a computer worm jointly developed by the U.S. and Israel, which sabotaged Iran’s Natanz enrichment plant by causing centrifuges to spin out of control. Unit 8200 (Israel’s elite cyber unit) was reported to be deeply involved in Stuxnet and related operations. The attack, though covert, ushered in a new era of cyber sabotage targeting critical infrastructure. In response, Iran began bolstering its own cyber forces. By 2011–2012, Iranian-state hackers emerged on the global stage: for instance, the “Iranian Cyber Army” defaced popular websites and Iran-linked hackers compromised the DigiNotar certificate authority to spy on Iranian dissidents’ Gmail accounts. By mid-2012, Iran was linked to Madi, an espionage campaign targeting hundreds of victims including 54 in Israel. These early attacks marked Iran’s “coming of age” in cyberwarfare, catalyzed in part by the shock of Stuxnet.
- 2013 – 2015: Retaliation and Espionage: Iran’s cyber activity accelerated, often in retaliation for sanctions or covert actions. Notably, Iran launched Operation Ababil, a series of disruptive denial-of-service attacks on U.S. banks in 2012-2013, and in 2014 Iranian hackers wiped computers at Saudi Aramco (the Shamoon virus) – signaling willingness to destroy data as political message. Within Israel, around 2014-2015, Iranian cyber units turned their sights on Israeli military and officials. A campaign uncovered in 2015 (code-named “Newscaster” by researchers) saw hackers from Iran’s Revolutionary Guard (IRGC) penetrate the personal computers of 1,800 key Israeli figures, including a former IDF Chief of Staff. Using spear-phishing emails loaded with spyware, they stole information from hard drives before Israeli experts intervened. In January 2016, Israel’s energy minister revealed a “severe cyberattack” on the Israel Electric Authority (power grid regulator) – an incident later assessed as a malware outbreak that was contained before damage occurred. Though details were scarce, it underscored the constant probing of Israel’s infrastructure. As one Israeli cybersecurity CEO noted at the time, it was “shocking” how even a high-tech nation like Israel was “at the receiving end of small to large scale cyber-attacks at such a rapid pace”.
- 2016 – 2019: Quiet Persistence and New Fronts: Throughout the late 2010s, cyber exchanges continued quietly. Israel reportedly carried out numerous covert cyber espionage operations against Iran’s military and nuclear projects (often unacknowledged publicly). Meanwhile, Iranian hackers broadened their reach. In 2017, Iran’s hacker group APT34 (“OilRig”) infiltrated Middle Eastern energy and telecom firms (some in Israel or allied countries) to gather intelligence. Iran’s use of cyber proxies also grew: contractors and ideological hacker crews working at arm’s length from the state. They engaged in data theft and surveillance, and occasionally, destructive attacks. For example, Iran’s MOIS (intelligence ministry) created APT39 for surveillance, and the IRGC’s Cyber Command oversaw groups like MuddyWater and Charming Kitten, which by 2018-2019 were identified phishing U.S. and Israeli targets (such as academic experts on Iran) to steal credentials. During this period, Israel was suspected in return of quietly foiling Iranian plots via cyber means – for instance, disrupting IRGC transport logistics and communications (reports hinted that Israeli intelligence hacked into Iranian systems to assist in locating and assassinating IRGC Quds Force commander Qasem Soleimani in 2020, although details remain classified). The cyber shadow war broadened beyond the two nations as well: Iranian hackers attacked targets in Saudi Arabia, the U.S., and Europe, and Israel allegedly cooperated with allies to counter Iran in cyber arenas beyond the Middle East.
- 2020: Escalation – Water Systems and Industrial Explosions: In 2020, the conflict entered a more disruptive phase with direct attacks on civilian infrastructure. In April 2020, hackers likely linked to Iran infiltrated Israeli water treatment facilities in a brazen attempt to manipulate chlorine levels and flow rates. Israeli officials revealed that six water and sewage facilities were targeted, causing pumps to malfunction and alarms to go off. The most serious breach involved Iranian-written code (routed through U.S. and European servers to mask origin) that accessed the controls of a major Israeli water pump station. Though quickly thwarted, officials warned that hundreds of civilians could have been poisoned or left without water during a heatwave if the attack had succeeded. Israel treated this quiet attempt to harm civilians as a crossing of red lines. The head of Israel’s National Cyber Directorate grimly warned that “cyber winter is coming, and coming even faster than I suspected,”predicting more such attacks on civilian life.Just weeks later, in May 2020, Israel retaliated in kind – albeit in a calibrated way. Then-Defense Minister Naftali Bennett authorized a cyber operation that crippled operations at Iran’s busy Shahid Rajaee port in Bandar Abbas for several days. Container traffic was thrown into chaos as shipping terminals and entry gates were paralyzed by a cyber-induced network outage. Satellite imagery showed miles of backed-up trucks. Israeli insiders framed the port hack as a “knock on the door” – a pointed reminder of Israel’s cyber capabilities, intended to deter further Iranian aggression without causing casualties. The tit-for-tat nature of these incidents was evident: covert cyber strikes were becoming a preferred tool for retaliation.That summer, Iran suffered a series of mysterious explosions and fires at sensitive sites – a pattern many attributed to Israeli cyber-sabotage or special operations. In late June and early July 2020, blasts rocked an Iranian missile production complex and the Natanz nuclear facility. At least some of these explosions are believed to have been triggered by cyber means. Iran’s atomic energy officials blamed Israel for the early July Natanz blast, which destroyed the power feed to advanced centrifuges and set back enrichment work by an estimated 9 months. While Israel never confirmed involvement, Israeli security sources hinted at a coordinated campaign to exploit Iran’s vulnerabilities and “prevent Iran’s nuclear progress,” even as they coyly noted “not every event that happens in Iran is necessarily us”. The cumulative effect by end of 2020 was clear: a shadow war of sabotage was fully under way, often with one cyber strike prompting a counter-strike.
- 2021 – 2022: Persistent Attacks and New Targets: The cyber exchanges only intensified. In April 2021, amid sensitive negotiations over Iran’s nuclear program, a sudden “accident” struck Natanz again – this time destroying the internal power system for the underground halls. Western intelligence attributed the sabotage to an Israeli cyberattack paired with an explosive device, calling it “nuclear terrorism”. Iran vowed revenge but found its options limited. Instead, that summer Iran’s hackers pursued other targets. In July 2021, Iran’s train system was hit by a cyber disruption that halted trains and defaced station signage with messages urging passengers to call the Supreme Leader’s office. Although Iran did not officially blame Israel, the attack’s cheeky psychological warfare style (“call Khamenei for info”) led many to suspect Israeli or allied hackers. A shadowy hacktivist group called Predatory Sparrow later claimed responsibility for disrupting Iran’s railway and other systems, hinting at insiders cooperating with foreign intelligence.In summer 2021, Iranian operatives also attempted to strike farther afield: U.S. authorities revealed that hackers linked to Iran’s government tried to breach the Boston Children’s Hospital network – a shocking attempt “to disrupt a hospital’s operations” that FBI Director Chris Wray called “one of the most despicable cyberattacks I’ve ever seen”. The attack, which exploited vulnerabilities in popular network software, was detected and foiled in time, but it underscored Iran’s willingness to target civilian infrastructure (even a children’s hospital) when under geopolitical pressure – in this case, during nuclear deal talks. Around the same period, Iranian state-sponsored groups stepped up espionage: for example, in October 2021, Microsoft exposed an Iranian campaign breaching dozens of defense-tech and maritime firms – including some tied to Israeli and Western militaries – to steal satellite and drone technology secrets. The hackers targeted about 250 companies worldwide, successfully compromising ~20, and even attempted to obtain commercial satellite imagery and shipping schedules to boost Iran’s military planning. This showed a new level of ambition and technical skill from the Iranian side, even as they continued more routine operations like disinformation or election meddling abroad.Late 2021 brought direct cyber pain to Iran’s populace again: in October, a massive cyberattack crippled Iran’s nationwide fuel distribution network. Gasoline subsidy smart cards stopped working, bringing 4,300 gas stations to a standstill and causing long queues. Iranian officials said 70% of stations were knocked offline. A group calling itself Gonjeshke Darande (“Predatory Sparrow”) claimed responsibility, stating the attack was carefully designed to avoid harm to life but to deliver a message to the regime. Iran openly accused Israel and the U.S. as the likely culprits behind this and a similar fuel-supply hack in 2021. Indeed, Israeli media reported that Predatory Sparrow had been linked to Israeli intelligence in the past. This unprecedented strike on Iran’s consumer fuel system demonstrated the potential for cyberattacks to create nationwide disruption – essentially a cyber blockade. Iran’s Supreme National Security Council had to step in, and it took 12 days for fuel card systems to fully resume normal operation. Notably, just weeks after, Iranian hackers (believed affiliated with IRGC) unleashed “Moses Staff,” a new hacking campaign against Israel. This group encrypted or deleted data at Israeli companies and leaked sensitive information with no ransom demand – purely to harm. By late 2021, Moses Staff had breached dozens of Israeli organizations (public and private), demonstrating a politically motivated wiper malware that signaled Iran’s intent to retaliate in cyberspace without even the pretense of criminal gain.Meanwhile, the tit-for-tat continued: In June 2022, a cyberattack (attributed by analysts to Israel or an allied hacktivist) struck Iran’s steel industry, forcing the shutdown of multiple major steel plants and even causing physical damage to a furnace. The incident, claimed by Predatory Sparrow, was accompanied by leaked security camera footage of an explosion in a steel mill – a rare glimpse of cyber-physical sabotage in action. Iran, for its part, was caught targeting Israeli civilians yet again in late 2022: an IRGC-linked group known as Agriusattempted to hack the systems of an Israeli hospital in November 2023 (in the northern city of Safed). Israeli authorities said the attack – which was carried out in collaboration with Hezbollah’s cyber unit – aimed to disrupt hospital operations and steal sensitive medical data. Thanks to early detection by Israel’s Cyber Directorate, IDF, and Shin Bet, the intrusion was stopped before patients were harmed, but some patient records were exfiltrated and dumped online. This marked an alarming escalation: Iranian cyber units working with Lebanese Hezbollah to target an Israeli hospital, explicitly putting civilian lives at risk.
- 2023 – 2025: The Floodgates Open? By 2023, the cumulative cyber onslaught had reached new heights, fueled by regional conflicts. Following a surge of Iran-backed militant activity against Israel (e.g. the Hamas war of October 2023), Iran and its allies launched a wave of cyber attacks on Israel. According to Israel’s National Cyber Directorate, Israel experienced a 43% increase in cyber attacks in 2023 compared to the previous year. Over 13,000 cyber incidents were recorded, with 3,380 deemed significant and around 800 of those having high destructive potential. The attacks spanned sectors – from waves of phishing and social media hacks to disruptive malware that aimed to destabilize critical services and supply chains. Notably, many of these operations were coordinated jointly by Iran and Hezbollah, and they increasingly focused on causing real-world damage (for instance, targeting hospitals, power utilities, or logistics firms) rather than just defacing websites. In response, Israeli-aligned hackers (sometimes appearing as independent hacktivists) struck back hard against Iranian infrastructure and financial systems. One pro-Israel group, Predatory Sparrow, claimed credit for a destructive hack on Iran’s largest state-owned bank (Bank Sepah) in mid-2025 that wiped data and disrupted services. The same group allegedly drained $90 million in cryptocurrency from Iran’s Nobitex exchange and dumped its source code online. Other reports in 2025 described Iranian state TV broadcasts being hijacked to show anti-regime messages amid nationwide Internet blackouts in Iran – presumably the work of Israeli cyber units or allied activists.By June 2025, the cyber hostilities had become entwined with real-world conflict. When Israel and Iran teetered on the brink of open war (with missiles and airstrikes reported), officials warned that the cyber front was primed to spill beyond the region. The U.S. Department of Homeland Security issued alerts that Iran might retaliate against Israeli strikes by hacking U.S. power grids, water plants, or other critical networks, exploiting the global interconnectedness of systems. Indeed, Iran’s track record of hitting civilian infrastructure in other countries – from Middle East oil companies to American local governments – has raised alarms. In late 2023, the U.S. had to sanction IRGC cyber officials for attacks on American water systems, after Iranian hackers breached PLC controllers at a small water authority in Pennsylvania, using an Israeli-made controller’s default passwords. Such incidents highlight that the Israel-Iran cyber feud can easily entangle other nations. As of 2025, constant cyber aggression is the new normal between Tehran and Jerusalem – most attacks still occur in the shadows, but their cumulative impact is more visible than ever.
The True Frequency and Scale
Putting it all together, the true scale of Israel-Iran cyber sabotage operations is far greater than publicly acknowledged. Major incidents like Stuxnet (2010), the Iran oil terminal hack (2012), the Saudi Aramco wipe (2012), or the Natanz explosions (2020, 2021) are just the tip of the iceberg. For each headline-grabbing attack, dozens of smaller or foiled operations have occurred:
- Many attacks never officially confirmed: Both governments often deny or downplay cyber incidents to avoid appearing vulnerable. For instance, when Iran’s Shahid Rajaei port was hit in 2020, Tehran acknowledged only a “cyber disruption” while satellite images showed widespread chaos. Similarly, Israel rarely publicizes thwarted attacks; the full extent of the April 2020 water system breach only became known through leaks to media and Western officials months later. Analysts rely on whistleblower accounts and leaked intel to piece together these covert battles. In one case, an apparent Israeli operation in 2018 to foil an ISIS plot was disclosed by a rare Unit 8200 public statement, hinting at cyber capabilities normally kept secret. Overall, for every attack we know about, others occurred in silence or under heavy cover of “plausible deniability.”
- “Failed” operations and near-misses: Not every attempt succeeds – but even failures can be instructive. Israeli officials have cited instances of Iranian malware discovered in utility networks before it could do damage, thanks to improved monitoring. Conversely, Iranian CERT teams have likely caught and cleansed Israeli spyware in some Iranian networks quietly. One public example: in 2018, Iran claimed to have detected and halted a new variant of Stuxnet before it could spread (though independent confirmation was lacking). There have also been cyber misfires, like malware that hit unintended targets – for example, an aggressive Iranian wiper in 2020 accidentally spread to companies in Europe, alerting researchers to its presence. These near-misses, seldom reported, show that the cyber struggle is continuous and iterative, with each side probing for weaknesses daily.
- Leaked documents and OSINT revelations: Some of the best insight into this hidden war has come from leaks. The Snowden files in 2013 hinted at deep U.S.-Israeli collaboration in offensive cyber (e.g. NSA and Unit 8200 exchanging tools), which was likely leveraged against Iran. In 2021, a massive leak of videos from Iranian prison CCTV (claimed by hacktivists) embarrassed Tehran’s security apparatus – and was speculated to be enabled by Israeli intelligence as psychological warfare. More directly, in 2022 a hacktivist front (Sharp Boys) leaked footage from the Iranian nuclear chief’s home security camera, suggesting Israeli surveillance deep in Tehran. On the other side, Iranian hackers (possibly Black Shadow, linked to IRGC) leaked personal data of Israeli civilians – including an LGBTQ dating site’s user database and an insurance company’s records – to sow discord and fear in Israeli society. Each leak offers a rare glimpse behind the curtain of what each side is infiltrating. For instance, a 2015 Iranian leak of emails from an Israeli general indicated IRGC briefly accessed an IDF military system. And the 2023 U.S. advisory about IRGC hackers targeting Israeli-made PLCs came with technical indicators, confirming Iranian cyber spies had obtained Israeli industrial equipment schematics to craft exploits. Such details, when pieced together, map an extensive, ongoing campaign of mutual cyber espionage and sabotage that is far more frequent than most realize.
In sum, the shadow cyber war between Israel and Iran is not an occasional skirmish but a continuous theater of conflict. Both nations appear to be engaged in rolling cyber campaigns – a strategic cat-and-mouse of infiltration, disruption, and counterattack. As a 2020 Atlantic Council brief observed, these are “fleeting glimpses of continuing cyber campaigns” rather than isolated “bolt from the blue” strikes. The true scale likely numbers hundreds of attacks and intrusions every year, ranging from minor website defacements to attempted infrastructure sabotage. Each incident, whether publicized or not, contributes to an escalating cycle that has proven difficult to deter or de-escalate.
Elite Cyber Units: Unit 8200 and IRGC Cyber Command – Evolution and Tactics
Behind these cyber offensives are highly skilled state actors. On Israel’s side, the tip of the spear is the famed Unit 8200, and on Iran’s side, the IRGC’s cyber units (often referred to collectively as the IRGC Cyber Command, alongside Ministry of Intelligence (MOIS) cyber teams). Both have evolved significantly in scope and tactics over the last decade, albeit in very different ways. This section explores each side’s cyber forces – their structure, recruitment and training, use of proxies, and trademark tools or exploits – to understand the engines driving the Israel-Iran cyber conflict.
Unit 8200: Israel’s High-Tech Military Hackers
Often likened to the U.S. NSA in its capabilities, Unit 8200 is a secretive Israeli Military Intelligence unit responsible for signals intelligence and cyberwarfare. It has a near-mythical reputation as “the best of the best” in cyber operations. Indeed, Unit 8200’s ranks are filled with young, elite recruits – top math and computer talents scouted from Israeli high schools through aptitude tests and then fast-tracked into intensive training. The unit’s “youthful, startup-like culture”emphasizes creativity and out-of-the-box solutions to unprecedented tech challenges. Veterans describe an environment where a 20-year-old analyst might be tasked with inventing novel ways to hack into a target’s system – “whether it’s a software weakness, encryption, or hacking into something, you must be capable to do it on your own,” as one graduate recounted.
Over the last decade, Unit 8200 has grown both in size and mission scope. Traditionally focused on electronic surveillance (phone calls, radios, etc.), the unit expanded heavily into offensive cyber operations in the 2000s, spearheading projects jointly with Mossad and NSA. Stuxnet’s development around 2007–2009 was a watershed: Unit 8200 officers were reportedly involved in writing code and deploying the virus into Iran’s Natanz facility (with the CIA/NSA). Cyber-sabotage became a core competency. In a rare disclosure, the IDF in 2018 acknowledged that Unit 8200 conducted “technological attacks and strikes” to preempt threats, citing how the unit helped thwart an ISIS plot by hacking the terrorists’ communications. This hints at its broad mandate: from classic espionage (intercepting adversaries’ secrets) to digital counter-terrorism and preemptive strikes through malware.
Key attributes of Unit 8200’s operations include:
- Advanced tools & zero-day exploits: Israel is known for its world-class cyber technology, and Unit 8200 has access to cutting-edge exploits. For example, Stuxnet employed at least four zero-day vulnerabilities in Windows systems – highly rare and valuable exploits at the time – enabling it to stealthily penetrate and propagate. Israeli cyber units have since been linked to other sophisticated malware like Duqu and Flame (espionage tools found in Iranian networks in 2011-2012), and Wiper malwares that physically disrupt equipment. Unit 8200’s arsenal likely includes custom malware tailored to industrial control systems (as evidenced by their role in Stuxnet) and hard-to-detect spyware. Notably, Israel’s thriving private cyber sector acts as an unofficial extension of Unit 8200: many Israeli cyber startups are founded by 8200 alumni, and some have developed exploits later used in state operations. A prominent example is NSO Group, founded by Israeli veterans, which created the Pegasus spyware – a “zero-click” tool that can remotely compromise smartphones. Pegasus has reportedly been used to monitor Iranian targets’ communications, among others, via third-party countries that obtained the tool. Another example is sold exploits for SCADA/ICS systems: Israeli companies staffed by ex-8200 experts have built backdoors into industrial controllers (some disguised as legitimate software updates) that could be leveraged in sabotage. In short, Unit 8200 benefits from an ecosystem where top talent and private innovation funnel into Israel’s offensive capabilities.
- Recruitment & training: Unit 8200’s recruitment is famously selective. Teenagers with exceptional STEM skills are identified through exams and a tech-oriented high school program (Magshimim). Those who pass muster undergo an arduous training pipeline in intelligence analysis, programming, and cyber-attack techniques. An alumnus described the challenge: “the problems we face have often never been seen before, so we need brilliant people who can invent solutions”. The unit has a high turnover – soldiers typically serve for a few years in their early 20s and then many enter the private sector (which in turn spreads their know-how to Israeli tech companies). This churn means Unit 8200 is constantly injecting fresh skills, staying on the cutting edge of emerging tech (AI, quantum encryption, etc.). It also means a network of alumni in industry who can be tapped if needed for reserve duty or contracted projects.
- Collaboration and contractors: While a military unit, 8200 often works intimately with Mossad (Israel’s foreign intelligence) for overseas operations, and with an array of private contractors. In recent years, Israel has increasingly leveraged private cyber companies to carry out or support operations under government direction. This allows deniability and accesses specialized expertise. For instance, Candiru and Quadream (Israeli firms) have developed exploits to hack computers and phones; though nominally private, their client list often aligns with Israeli strategic interests. Contractors also assist in analyzing stolen data or running influence operations online. By using mercenaries or outsourcing certain tasks, Unit 8200 can extend its reach globally without directly deploying soldiers. However, it tightly oversees these partnerships through the Ministry of Defense export controls and by embedding former 8200 officers in key companies.
- Signature tactics: Over time, Unit 8200 has honed specific tactics. One is supply chain attacks – infiltrating hardware or software destined for the target. Reuters revealed an operation (with Mossad) that inserted explosive or surveillance devices into thousands of Hezbollah’s imported pagers and radios, causing devices to literally blow up or transmit enemy positions. Unit 8200 handled the technical insertion of these “implants” at the manufacturing source. This blend of physical and cyber sabotage is a hallmark of Israeli ingenuity. Another tactic is precision targeting: Israeli cyber strikes generally aim to minimize collateral damage. For example, in the 2023 Predatory Sparrow attacks on Iran’s gas stations, the group (widely presumed to be Israel-aligned) claimed they designed the malware to avoid harming emergency services while causing maximum disruption to consumer fuel supplies. Likewise, the May 2020 port hack was calibrated to cause economic loss but no casualties. This suggests Unit 8200 operations undergo careful legal and strategic review – likely to avoid giving Iran justification for all-out war. Lastly, Israel excels in integrated cyber-kinetic operations: using cyber intrusions to facilitate physical actions. Israeli hackers might disable alarms, cut communications, or feed false data to cover for an airstrike or an agent on the ground. The 2021 Natanz blast is suspected to have involved cyber manipulation of power systems to amplify the physical explosion. Such complex ops show the maturation of 8200’s playbook.
IRGC Cyber Command and Iran’s Hacker Ecosystem
Facing off against Unit 8200 is Iran’s cyber apparatus, dominated by the Islamic Revolutionary Guard Corps (IRGC). Iran’s journey in cyberwarfare started later and from a weaker base, but it has made rapid strides in both capability and boldness – especially after being on the receiving end of attacks like Stuxnet. The IRGC, a military force independent of the regular army, took the lead in offensive cyber operations as part of its mission to defend the Islamic Revolution from foreign and domestic enemies. Over the past decade, the IRGC’s cyber arm has grown from a nascent program to a sprawling network of units and proxies. Key characteristics include:
- Structure and units: The IRGC operates a Cyber Command (sometimes called the Cyber Electronic Command, IRGC-CEC), which coordinates major offensive campaigns. In 2023, the U.S. identified and sanctioned the head of IRGC-CEC, Brigadier General Hamid Reza Lashgarian, and five other IRGC cyber officials for directing attacks on Western critical infrastructure. This indicates a formal hierarchy at work. Within the IRGC, several known groups carry out operations:Iran’s structure thus is a mix of formal military units and semi-autonomous teams that often present themselves as independent “hacktivists.” This diffuse structure provides plausible deniability, a feature Iran exploits to avoid direct blame. When confronted, Iranian officials routinely claim their cyber posture is “purely defensive” and dismiss accusations (even the well-evidenced water poisoning plot) as baseless. In reality, the IRGC and allied hackers are very active offensively, but they operate behind layers of cut-outs.
- “Cyber Avengers” (Cyber Av3ngers): an IRGC-affiliated group active since mid-2010s, resurrected in 2023 to target Israeli and U.S. critical infrastructure (notably exploiting Israeli-made PLC controllers in water systems). They act as a pseudo-hacktivist outlet for IRGC, often leaving messages like “Down with Israel. Every equipment ‘made in Israel’ is our legal target.”.
- APT33 (aka Elfin or Magnallium): An IRGC-linked hacking unit known for attacks on oil & gas and aviation sectors in Saudi, U.S., and possibly Israel. They developed custom malware (Shamoon wiper) and probed industrial control systems.
- APT34 (OilRig): Likely MOIS-run but coordinates with IRGC, focused on Middle East government and telecom targets, including attempting intrusions into Israeli networks via phishing.
- APT35 (Charming Kitten/Phosphorus): An IRGC unit specialized in social engineering; they famously impersonate journalists or scholars to trick targets into revealing passwords. They have targeted Israeli academics and defense researchers often.
- APT42: A subgroup identified by Mandiant, tasked mainly with surveillance of Iranian dissidents abroad but also involved in the bold 2022 cyberattack on Albania’s government (as retaliation against the MEK opposition group). APT42’s use of ransomware as a political tool in Albania – dropping fake ransom notes while actually aiming to destroy data – mirrors tactics later used against Israel.
- MuddyWater (Seedworm): Believed to be a contractor group working for IRGC, MuddyWater conducted an attempted ransomware campaign on Israeli companies in 2020, but with no intent to collect ransom – suggesting a cover for destructive goals. Microsoft assessed MuddyWater as part of Iran’s Ministry of Intelligence apparatus.
- ‘Fox Kitten’ coalition: A name given to an IRGC initiative uniting various groups (APT33, 34, 35) to exploit common vulnerabilities and establish persistent footholds in target networks worldwide. Operation Pay2Key in late 2020, which hit dozens of Israeli companies with ransomware, was attributed to this Fox Kitten group. In several cases, Pay2Key hackers refused payment and simply leaked stolen data, underlining an ideological motive to damage Israeli interests.
- Recruitment and training: Lacking the tech base of a nation like Israel, Iran has taken a different path to build cyber talent. The IRGC has leveraged the Basij (a paramilitary youth organization) and university programs to spot and recruit skilled programmers and engineers. Cyberwarfare units are believed to cherry-pick top computer science graduates from Iran’s universities (e.g. Sharif University) by offering them lucrative or ideologically appealing roles. Additionally, Iran has embraced patriotic hackers – individuals or gangs who already conduct attacks aligned with regime interests. After 2009’s Green Movement protests, for example, the so-called “Iranian Cyber Army” (likely supervised by the IRGC) emerged to attack opposition websites. The regime realized it could harness such actors. The Basij Cyber Council was formed to mobilize tens of thousands of student hackers in a reserve-like capacity. They may not all be sophisticated, but they add volume – defacing sites or amplifying propaganda. The IRGC also isn’t shy about hiring talent from the criminal underground. U.S. indictments have revealed Iranian hackers who engaged in cyber crime (credit card theft, etc.) but were tolerated or later recruited by the state. For instance, nine Iranians indicted in 2018 for stealing academic data across the West were contractors for the IRGC. This blur between state and criminal actors means Iran’s cyber ranks can expand without all operatives being formal IRGC officers.
- Use of proxies and mercenaries: Iran has perfected the use of third-party groups and foreign proxies in cyber operations:
- Hacktivist fronts: Groups with names like Cyber Avengers, Cyber Tigers, Imam Reza Cyber Corps, etc.periodically surface to take credit for attacks on Israel or the U.S. These groups often have Telegram channels and issue fiery communiqués. They give Iran a way to signal or brag about attacks while maintaining deniability. For example, Cyber Av3ngers took credit (with telling anti-Israel rhetoric) for the late-2023 hacks on U.S. water systems using Israeli PLCs. Iran can claim these are independent activists, even though Western agencies have tied them back to IRGC control.
- Allied militant groups: Iran’s regional proxies like Hezbollah in Lebanon, Kataib Hezbollah in Iraq, and Hamas in Gaza have been developing their own cyber units, often with Iranian training. Hezbollah’s so-called “Lebanese Cedar” cyber unit worked with Iran’s MOIS on espionage; by 2023 Hezbollah hackers were directly collaborating in attacks on Israeli targets (as seen in the hospital case). This effectively outsources some of the cyber campaign to allied organizations. It also means Iran’s cyberwar dovetails with its proxy wars. Israeli defense sources noted in 2023 that Iran and Hezbollah operated in tandem in an onslaught of cyber attacks following a Hamas-Israel clash.
- Criminal ransomware gangs: Distinct from ideological hacktivists, some Iranian groups are financially motivated but tacitly supported by the state. The Black Shadow crew, for instance, hacked Israeli companies like an insurance firm (Shirbit in 2020) and extorted them in Bitcoin, leaking data when unpaid. Though never officially linked to IRGC, the choice of Israeli victims and lack of fear of reprisal suggest regime blessing. Iranian hackers have also been spotted on dark web forums sharing Western network accesses and malware tools. Iran might not directly hire foreign mercenaries (e.g. Russian or North Korean hackers), but intelligence reports indicate some cooperation and tool-sharing in the murky cybercrime world. For example, Iranian operatives have utilized hacking tools leaked by others – a notable case being when Iranian APTs incorporated parts of leaked NSA cyber weapons (from the 2017 Shadow Brokers leak) into their own malware, accelerating their capabilities.
- Tools, malware, and exploits: In terms of cyber arsenal, Iran’s approach has been characterized by creativity on a budget. Lacking the vast zero-day research pipeline of Unit 8200 or NSA, Iranian hackers often rely on social engineering, known vulnerabilities, and stealthy techniques:
- Spear-phishing and credential theft are a staple. As noted, groups like Charming Kitten craft fake personas (journalists, colleagues) to trick targets into giving up passwords. In one case, they even conducted long correspondence with targets for weeks before sending a malicious link. Such patience reflects training.
- Malware strains attributed to Iran run the gamut: Shamoon (wiper malware that destroyed 35,000 computers at Saudi Aramco in 2012) was their first big splash. Since then, they’ve developed other wipers like StoneDrill, ZeroCleare, and more recently Apostle (which posed as ransomware but was actually destructive, used against Israeli targets in 2020). They also use custom Remote Access Trojans (RATs) like Moses Staff’s “StrifeWater” RAT which establishes hidden backdoors in Israeli networks.
- “Living off the land” tactics: Iranian APTs frequently abuse legitimate admin tools (e.g. PowerShell, WMI) to carry out attacks without needing custom malware. This makes attribution harder and detection more difficult, a strategy called Living off the Land. For example, the MuddyWater group is known for heavy use of PowerShell scripts as backdoors, and for using open-source or stolen tools to cover their tracks.
- Known exploits and occasional zero-days: Iranian groups have shown adeptness at quickly using known exploits (often called N-days). When a critical vulnerability in VPN or email server software is disclosed, Iran is often among the first to mass-scan and compromise unpatched systems globally. For instance, in 2021 Iranian hackers exploited a known Fortinet VPN flaw to break into networks – including the attempt on the Boston hospital. They also capitalized on the 2021 Microsoft Exchange Server zero-day spree to breach organizations in Israel, the U.S., and elsewhere (as evidenced by some indictments). While Iran has not been publicly tied to many original zero-day discoveries, there are signs they invest in this area too: a Microsoft report in 2022 noted Iranian state hackers have begun using generative AI to speed up vulnerability research and exploit development. And Google’s Project Zero has listed a few 0-day exploits likely used by Iranian actors in recent years. So while Iran’s toolkit historically relied more on readily available exploits, they are evolving to deploy more advanced techniques as needed.
In terms of tactics, Iranian cyber operations have become more bold and disruptive over time – moving from espionage and website defacements a decade ago to critical infrastructure sabotage and data destruction today. Yet, experts assess that Iran’s top capabilities still “are not at the level of the Israelis or Americans”. Israel’s defenses and cyber prowess outmatch Iran’s in pure technical terms. However, Iran leverages asymmetry: it can tolerate more risk and use deniable proxies to punch above its weight. The IRGC’s cyber command effectively engages in a form of digital guerrilla warfare, where persistence and ideological fervor sometimes compensate for a deficit in high-end tech.
One striking pattern is how Iran’s cyber units have learned from each confrontation. After Stuxnet, they rapidly grew offensive talent (leading to the wave of attacks on U.S. banks and Gulf states in 2012-13). After the 2020 water facility incident and Israeli reprisals, Iran attempted more civilian-targeted hacks (fuel system, hospital). As Israeli and U.S. defenses harden, Iran diverts to “softer” targets or uses global proxy networks (like the 2023 focus on poorly secured U.S. municipal systems via Cyber Avenger). The interplay between Unit 8200 and IRGC hackers is almost Darwinian – each forcing the other to adapt. Unit 8200, for its part, has also broadened its tactics, increasingly targeting Iran’s financial arteries (banks, crypto exchanges) and internal communications to create unrest, as seen by recent hacks that triggered Internet shutdowns in Iran.
In summary, Israel’s Unit 8200 and Iran’s IRGC Cyber Command represent two of the most active cyberwar units in the world, each with distinct strengths. Unit 8200 brings top-notch talent, innovation, and a fusion of state and private resources to achieve pinpoint strikes. The IRGC brings numbers, determination, and a willingness to flout norms by aiming at civilian infrastructure or by using any available means (including criminals and global malware) to hit back at its adversary. Together, they have turned the Middle East into one of the primary battlegrounds for state-sponsored cyber conflict – with tactics and tools that are now proliferating globally as other actors observe and copy them.
Sleeper Malware and Infrastructure Backdoors: Prepositioning for a “Cyber Pearl Harbor”
One of the gravest concerns in this Israel-Iran cyber struggle is the prospect that each side may have already seeded the other’s critical infrastructure with hidden malware – “sleeper” code that lies dormant inside power grids, water systems, transport networks or financial systems, awaiting a signal to activate. Such pre-positioned backdoors could be a game-changer in the event of an all-out war, enabling swift and devastating sabotage at the outbreak of hostilities. How real is this risk, and what evidence exists of these silent infiltrations?
Penetration of Critical Infrastructure
Both Iran and Israel have undoubtedly attempted to hack into each other’s critical infrastructure networks on multiple occasions. We have several confirmed examples that suggest these penetrations, and likely others undisclosed:
- Water Systems: The April 2020 Iranian cyber-attack on Israeli water facilities was not just a one-off hit; it indicated a broader campaign to map and compromise water infrastructure. Israeli investigations after the incident found that the attackers had routed their malicious code through servers in the U.S. and Europe, using the access to manipulate industrial control software in pump stations. This implies the Iranians had prior access or knowledgeof those systems (possibly via earlier hacks or by researching remote-access interfaces). Even though Israel promptly changed passwords and reduced internet connections for its water facilities after the attack, the attempt raises the question: could Iran have planted other backdoors in less obvious water or sewage systems? Separately, in late 2023, U.S. officials revealed that the IRGC-linked Cyber Av3ngers breached an American municipal water plant’s control systems (using vulnerabilities in Israeli-made PLC controllers). The hackers defaced the systems with anti-Israel messages but could just as easily have altered water treatment settings. This shows Iran’s capability to quietly insert itself into water infrastructure abroad. It is reasonable to suspect they have tried to do the same to Israeli water utilities, perhaps in stealthier ways than the noisy April 2020 attempt. Conversely, Israel – whose intelligence once reportedly hacked into an Iranian dam’s control software (a U.S. dam in New York was also infamously breached by Iranian hackers in 2013, illustrating the interest in dam control) – likely has probed Iran’s water management networks. Iran’s water infrastructure is somewhat less digitized in rural areas but major reservoirs and pipelines are centrally monitored, offering targets.
- Electric Power Grids: Power infrastructure is a high-impact target in wartime. While no public instance of Israel turning off Iran’s grid via cyberattack is confirmed, there are suggestive pieces. For example, the 2021 Natanz strike that knocked out electrical power to the nuclear facility hints at a cyber component that took down part of Iran’s regional power supply. In 2019, media reports (citing U.S. officials) claimed that the U.S. Cyber Command and possibly Israel had implanted “implants” or logic bombs in Russia’s power grid as a deterrent. It’s plausible Israel has similarly planted malware in Iran’s electric grid control networks – as a form of insurance. Such an operation would be clandestine and only executed if, say, Iran was about to launch missiles at Israel (cyber means could then disrupt launch communications or grid power to slow military mobilization). On the flip side, Iran has repeatedly attempted to breach Israel’s power companies or grid operators. One known case: in January 2016, Israel’s Electric Authority was hit by a malware attack, which officials implied might have been of Iranian origin (coming just weeks after Iran had been blamed for attacks on Ukraine’s grid and U.S. networks). Although that specific incident caused no outages, it underscores that Iranian cyber actors were targeting Israel’s power systems. Given years of opportunity since, it is quite possible that Iranian hackers have at some point gained persistent access to a segment of Israel’s electrical grid or distribution control system. Even a small foothold, if maintained covertly, could be escalated in a crisis to cause blackouts. The same holds for Israel – who would surely see value in being able to turn off lights in Tehran or disable Iran’s energy infrastructure remotely if conflict erupts.
- Oil, Gas and Petrochemical Systems: Iran’s economy and military rely heavily on oil and gas facilities. Israel (often with U.S. help) has targeted this sector via cyber before – for instance, the Stuxnet malware didn’t just hit Natanz; variants like Wiper and possibly Shamoon (v2) were suspected in unexplained fires or outages at Iranian petrochemical plants in 2016 and 2018. In mid-2020, a blast at an Iranian petrochemical site (Shiraz) and another at the Natanz centrifuge assembly center were rumored to be cyber-sabotage to hinder Iran’s industrial base. Iran, for its part, has struck at Israel’s energy-adjacent sectors: gas distribution in 2021 as noted, and attempted intrusions in other countries’ oil infrastructure as a proxy (e.g. 2014 attack on a Las Vegas Sands casino’s network, partly because its owner advocated strikes on Iran). If Iran could breach an Israeli offshore gas platform or rig’s systems, it could potentially trigger an explosion or spill. Both sides understand the catastrophic potential. Researchers have noted that while major energy facilities tend to be well protected, smaller suppliers or peripheral systems (like pipeline monitoring or regional substations) are more exposed, and once a hacker gains remote access there, they could move to more sensitive controls. In other words, vulnerabilities exist that skilled actors could exploit to implant sleeper malware in oil and gas operations.
- Banking and Financial Networks: Financial infrastructure can be a geopolitical pressure point. Israel’s banking sector is highly digitized and has been targeted by Iranian hackers seeking both disruption and espionage. In late 2020, the Pay2Key Iranian operation hit multiple Israeli banks and financial firms, stealing data and demanding ransoms (though the true aim seemed punitive). Israel managed to contain damage with help from cybersecurity firms. However, concern remains that Iran might plant logic bombs in financial transaction systems to corrupt data or drain funds. Conversely, Israel has shown it can strike Iran’s finance: the 2025 hacks of Iran’s Bank Sepah (clearing system disruptions) and the Nobitex crypto exchange (theft of funds) demonstrate a capability to breach even well-guarded financial servers. There is also the aspect of global financial messaging systems (like SWIFT): Iran’s banks were cut off by sanctions, but Iranian hackers have attempted to compromise foreign banks to evade sanctions or steal money (one case being a 2018 attempt on a UK bank via compromised credentials). As a sleeper tactic, either side could have placed undetected malware inside the other’s financial clearinghouses that could be triggered to scramble records, halt transactions, or siphon assets at a critical moment. The implications for economic stability are huge.
- Transportation (Air, Sea, Land): Transportation grids are another domain of interest. Israel’s 2020 port hack in Iran showed the impact on shipping; it’s conceivable Israel quietly also infiltrated Iran’s airline reservation or rail control systems to gather intel or prepare future sabotage. (Some cyber experts have suggested Israel’s intelligence likely penetrated Iran’s civil aviation databases to track Quds Force officers’ travels, etc., which could facilitate targeting). Iran’s hack on train networks in 2021, as well as an earlier 2019 incident where hackers (possibly Iranian) caused disruption to Iranian airline boarding systems, illustrate a focus on transit. While causing trains to stop or ships to queue is more nuisance than catastrophe, a sleeper malware in an air traffic control system or a busy port’s cranes could be extremely dangerous if activated (mid-air collisions or port accidents). Both Iran and Israel have robust air defense and radar networks as well – these too might be laced with backdoors (Israel in 2020 reportedly cyber-attacked Iranian air defense to assist armed drone strikes on Iran’s proxies in Syria). Any such stealth pre-positioning is understandably kept highly secret.
How Real is the Sleeper Threat?
The concept of “sleeper malware” – malicious code planted long before and left inert until an opportune moment – is a known strategic gambit in cyberwar. The U.S. and Russia have admitted to inserting dormant implants in each other’s power grids as a deterrent strategy. In the Israel-Iran context, evidence suggests both sides have at least attempted this strategy, though the success and current presence of such backdoors are uncertain.
Israeli officials have indirectly acknowledged the danger. After the 2020 water attacks, Israel’s Cyber Directorate urgently instructed all critical utilities to “reduce internet exposure” and tighten access, fearing unknown intrusions. This came amid intelligence that Iranian hackers had been scanning Israeli industrial networks for entry points. The fact that Iran’s April 2020 attack went as far as it did – accessing operational controls – means they likely had some persistent access or at least prior reconnaissance. Had the malicious code not been caught, it could have remained in systems to trigger a poisoning event later at Iran’s choosing. In essence, Iran attempted to plant a sleeper in water systems, and fortunately was discovered. How many other such attempts might have gone undetected?
On Iran’s side, one can look at the numerous unexplained accidents in Iranian infrastructure (nuclear facility glitches, refinery fires, pipeline explosions) and speculate that some may have been caused by malware with a time delay or a remote trigger. For instance, in 2018 a sudden explosion at an Iranian oil storage tank was rumored to be cyber-induced, possibly by reactivating some code left in a previous hack. Iranian cyber defenders have grown increasingly wary; Iran’s civil defense chief often warns about “software bombs” and they occasionally pre-emptively disconnect parts of networks if they suspect infiltration (e.g., Iran temporarily took its main oil export terminal offline in 2012 when a virus outbreak hit the Oil Ministry). These defensive moves indicate Iran believes sleepers might lurk in its systems, placed by Israeli or Western actors.
From an outside perspective, the risk is indeed real. A senior U.S. official in 2023 emphasized that Iranian cyber attacks on critical infrastructure demonstrate a persistent threat, and that even “unsophisticated” breaches can succeed if defenders aren’t vigilant. Basic cybersecurity gaps – weak passwords, outdated software – can enable an adversary to get in and quietly maintain access for months or years. A chilling scenario would be during a future military crisis: Israel’s cities suffer mysterious power outages or telecom failures as missiles are flying, or Iran’s command-and-control networks collapse just as its forces mobilize – all caused by those hidden cyber “sleeper cells” coming to life.
Concrete examples are limited (for secrecy reasons), but one reported incident in 2023 gives a flavor: U.S. investigators found that Iranian hackers had implanted malware on the networks of a small water facility in Pennsylvania and other sites, lying in wait. As the White House noted, this “demonstrated the persistent threat from hostile countries like Iran” and how such intrusions could have “life-safety impact” if not purged. It does not stretch the imagination to assume similar implants might exist on Israeli soil. Indeed, former U.S. CISA Director Jen Easterly noted in 2025 that Iran has a track record of cyber retaliation against civilian infrastructure (water, financial systems, energy, etc.) and that one must assume they have pre-positioned access in some of these networks ready to use when directed.
Both Israel and Iran also have to consider that activating a cyber doomsday switch carries huge risks. If Iran triggers a sleeper malware to cause say, a prolonged blackout in Tel Aviv, Israel could view it as an act justifying forceful retaliation (potentially even kinetic). Likewise, if Israel plunges Tehran into darkness or derails trains causing civilian harm via cyber, Iran might respond with missiles. This raises the threshold: such cyber backdoors might be held in reserve as an ace card or deterrent, rather than used lightly. But as tensions rise, the temptation to use them rises too.
In summary, while secret by nature, the evidence points to an ongoing race to penetrate and “camp out” inside critical systems. The main vulnerabilities exploited so far include:
- Human factors – default or weak passwords on industrial controllers (as with the Unitronics PLC case), phishing employees for remote access credentials, etc.
- Legacy systems and connectivity – many infrastructure controls were not designed with security and have been retrofitted online. Researchers found some Israeli water and power HMIs exposed to the internet in 2020, which could be hacked to alter pumps or valves.
- Supply chain compromises – inserting backdoors in hardware or software updates. This is a plausible vector for Israel in Iran: e.g. Iranian utilities using imported equipment (Chinese or European) that Israeli intelligence can tamper with before delivery. Iran likewise might target technology that Israeli companies use (through third-party software compromises like the SolarWinds-style attacks).
- Insider recruitment – Always a possibility, albeit less discussed in cyber context. Iran’s agents or proxies could attempt to bribe or coerce an Israeli technician to insert a USB with malware in a control system (or vice versa – Israel could exploit Iranian insiders to deploy malware devices directly, which is believed to be how Stuxnet initially entered Natanz).
The bottom line is that both nations likely have some degree of persistent cyber foothold in each other’s infrastructure, even if fragmentary. The full extent won’t be known unless a major war “lights up” these latent threats. However, given the demonstrated incidents and warnings by officials, neither nation can afford to assume that their critical networks are clean. As one Israeli cyber chief ominously framed it after detecting Iran’s water attack: the era of silent infiltration means a “cyber winter” could arrive suddenly. In practice, that means Israel and Iran are each living with a potential Trojan horse in their midst – a dangerous cyber sword of Damocles hanging over their civilian populations.
Third-Party Players: Proxies, Cybercriminals, and the Dark Web in the Shadow War
The Israel-Iran cyber conflict is not confined to the actions of official state units alone. A striking feature of this shadow war is the involvement of third parties – ranging from other nation-states and intelligence agencies, to non-state hackers, mercenaries for hire, cybercriminal networks, and even dark web elements. These actors can amplify, finance, or obscure the true perpetrators of cyber operations, creating a complex web of attribution and proxy battles. Here we examine the role these third parties play, including the use of cryptocurrencies and illicit markets to fund or launder operations, and the phenomenon of “false flag” attacks.
Proxy Hacker Groups and “Hacktivists”
Both Iran and Israel have made extensive use of proxy groups: ostensibly independent hackers or hacktivists who carry out attacks aligned with their patron’s interests. These groups provide a cloak of deniability and can be disavowed if convenient.
- Iran’s hacktivist fronts: Iran arguably pioneered the state-backed hacktivist model. As mentioned, the Iranian Cyber Army emerged in 2009-2010 to attack dissident sites and even foreign targets like Twitter and Voice of America. Since then, Tehran’s cyber strategy explicitly leverages such cut-outs. Recent examples include:These proxies allow Iran to conduct deniable cyber warfare. If caught, officials can say “that was a rogue group, not us.” In practice, the lines are blurry: Check Point’s analysis noted at least four major Iranian hacktivist groups active in 2023 that coordinate narratives with Iran’s strategic aims. They often brag about attacks immediately on social media, which state media can then quote as external sources. This layered approach helps Iran handle public perception and potentially avoid direct retaliation, since attribution might be fuzzy.
- Cyber Av3ngers: Re-appeared in 2023 as a Telegram-based outfit loudly claiming responsibility for hacking Israeli or U.S. critical infrastructure. They framed their attacks as retaliation, tying U.S. targets to Israel by saying “any equipment made in Israel is a target”. U.S. government alerts confirmed this group’s linkage to IRGC and its activity of exploiting PLCs en masse in late 2023.
- Cyber-Toufan and Haghshenas (or Haghjoyan): These are other IRGC-affiliated hacktivist brands that popped up around the 2023 conflict, extending attacks beyond Israel to U.S. entities. They often recycle old leaked data or make exaggerated claims to boost their profile (an Iranian playbook to create the perception of widespread capabilities).
- Moses Staff: As discussed, this group surfaced in late 2021, conducting ransomware-like attacks on Israeli infrastructure without seeking profit. It is believed to be run by Iranian or Hezbollah hackers under an ideological guise. Moses Staff explicitly frames its mission as anti-Zionist (“targeting Israeli companies… with the goal of espionage and disruption”). It’s a classic hacktivist persona masking state directives.
- Homeland Justice: A front used in the 2022 Albania cyberattack, posing as angry citizens upset with MEK dissidents. It served to muddy the waters around IRGC’s involvement by adding a faux grassroots veneer.
- Israeli-aligned hacktivists: Israel traditionally kept cyber operations in-house (Unit 8200/Mossad). However, there are signs of an emerging pro-Israel hacktivist ecosystem, possibly in response to Iran’s use of the same. The most notable is Predatory Sparrow, which, while mysterious, has claimed hacks that clearly align with Israeli interests (Iran’s steel plants, railways, bank, etc.). Predatory Sparrow’s communications sound like an activist group – they justified their 2021 and 2022 attacks as responses to Iranian aggression and took care to avoid civilian harm. Some experts believe Predatory Sparrow could be a front for Israeli military hackers or a joint intel operation between Israel and dissident Iranians. By not officially being Israel, this group gives Israel plausible deniability for bold actions that might otherwise be considered acts of war. For example, draining $90 million from an Iranian exchange (as Predatory Sparrow boasted in 2025) might be considered financial terrorism if done openly by a state. But as a hacktivist claim, it muddies the legal waters. Similarly, there have been loosely affiliated pro-Israel hacker collectives (some linked to the Anonymous movement) that occasionally deface Iranian sites or leak data from Iranian ministries. Israel’s government does not officially acknowledge them, but there have been wink-and-nod moments where officials say they “won’t shed a tear for anonymous hackers helping expose the Iranian regime.”This suggests a quiet tolerance or even encouragement.
- Other states’ proxies: The Iran-Israel cyber fight also draws in proxies of other nations. For instance, Iran’s close ties with North Korea’s hackers have been hinted at – North Korea has sold weapons to Iran, and some cybercrime collaboration (like shared techniques in cryptocurrency theft) has been posited by analysts (North Korean groups are similarly skilled at crypto heists which Iranian actors started doing). There’s also Russia: while Russia stays officially neutral, some Iranian malware (e.g. parts of the Triton industrial malware used in Saudi Arabia 2017) had fingerprints of Russian tooling, implying either cooperation or purchase of exploits. Israel, on its side, has allies like the US and UK whose cyber units (NSA’s Tailored Access Ops, US Cyber Command’s CNMF teams) have likely coordinated with Israel. For example, when Iran’s Islamic Revolutionary Guard’s networks were struck by a destructive U.S. cyberattack in June 2019 (in retaliation for drone shoot-down), some believed Israeli intelligence provided targeting help. Additionally, Arab Gulf states (like the UAE, Saudi Arabia) share Israel’s concern about Iran and have reportedly hired Israeli cyber mercenaries (ex-Unit 8200 operatives) to conduct surveillance on Iranian proxies or even Iran itself. In a twist, some of those mercenaries (through companies like DarkMatter, run by Emiratis with Israeli talent) ended up hacking Qatar and others, showing how messy third-party involvement can get.
Cybercriminal Networks and Dark Web Financing
Not all players in this conflict are motivated by ideology; some are in it for profit and can be instruments for either side:
- Ransomware gangs: The rise of global ransomware has created semi-organized networks of extortionists. Iranian hackers have been known to moonlight as ransomware attackers – for instance, the Dharma ransomware has been used by Iranian groups to make money off victims worldwide. These profits can fund their operations or be funneled into Iran’s sanctioned economy via crypto. Conversely, Israel has occasionally been targeted by ostensibly Russian ransomware gangs (like the Grief or Conti group) – raising suspicions that Iran or its ally Russia might have directed a hit behind the scenes, or simply that criminals see rich Israeli companies as targets. In 2020, an Iranian-linked group Black Shadow hacked an Israeli insurance firm and demanded a Bitcoin ransom of $1 million, eventually dumping all the data when unpaid. The use of crypto and the criminal nature gave Iran plausible deniability, even as Israeli officials assessed the attack as politically motivated. We also see Iranian hackers deploying wiper malware disguised as ransomware (e.g. Apostle, Pay2Key), which is a sort of reverse false-flag – pretending to be criminals when actually acting as agents of sabotage.
- Cryptocurrency and dark web markets: Cryptocurrencies have played a dual role. First, as mentioned, extorted funds via Bitcoin or Monero provide off-book financing. U.S. indictments have traced how Iranian hackers and fronts laundered Bitcoin through exchanges to convert ransomware payments into Iranian rials, bypassing sanctions. Second, crypto exchanges themselves became targets or conduits. The Nobitex hack (June 2025) robbed Iran’s largest crypto exchange of millions; this not only inflicted financial pain but also could have yielded intelligence on how Iran evades sanctions using crypto. On the dark web, one can find malware marketplaces and exploit brokers. Both Iranian and Israeli operatives likely monitor these forums. Iran, being resource-constrained, might purchase zero-day exploits or hacking services from dark web actors (some evidence shows Iran-affiliated hackers bought access to compromised servers from crime forums to use as launchpads for attacks). There’s also the sale of stolen data: Iranian groups have sold Israeli stolen data (like voter registration or dating site info) on dark web forums, or simply dumped it for propaganda. Israel’s services, for their part, might quietly patronize certain hacker forums to gain tools or intel; or even run fake personas offering malware to see who in Iran’s community takes the bait.
- Mercenary hackers (“hackers for hire”): A burgeoning industry of private hackers (often in India, Eastern Europe, etc.) offer hacking on contract. If a state wanted to distance itself, it could hire such mercenaries to hit a target. It’s hard to find concrete proof of Iran or Israel doing this (both have internal talent), but smaller scale tasks could be outsourced. For instance, phishing campaigns or DDoS attacks could be contracted out. Iran has been known to employ freelance Iranian hackers on a project basis, according to a 2022 U.S. DNI report – these individuals might do a paid job to break into a specific network and hand off access to IRGC handlers. On Israel’s side, intelligence agencies have historically hired foreign agents for on-the-ground ops; in cyber, they could similarly recruit non-Israeli hackers for plausible deniability (though again, the Israeli private sector covers a lot of that need legitimately).
False Flags and Attribution Games
In the smoke and mirrors of cyberwar, false flag operations – where an attacker poses as someone else – are a real hazard. Both Iran and Israel have engaged in deception to misattribute attacks:
- Iran’s hackers have sometimes pretended to be anti-Israeli or anti-Western hackers from other countries. A notable case: in 2019, two Iranian hackers indicted by the US had sent threatening election emails posing as the far-right Proud Boys to intimidate American voters. This was a political influence op masquerading as domestic extremist action. Similarly, when Iranian wiper malware hit Saudi Arabia, the malware’s code and even the name “Cutting Sword of Justice” were crafted to look like it might be a domestic Saudi dissident act, obscuring the Iranian hand.
- Israeli cyber operations often go to lengths to avoid leaving Israeli fingerprints. Stuxnet, for example, was a joint op but it masqueraded simply as a sophisticated malware, only through later forensic analysis were Israeli links presumed (like certain codewords referencing Biblical Esther). In more recent attacks by Predatory Sparrow, the group issues statements in Farsi targeting the Iranian regime – presenting as an indigenous dissident group fed up with the government. This false flag as domestic opposition can sow confusion in Iran: was it Israel or internal rebels? Perhaps both? In any case, it dilutes the narrative that Iran is under external cyber attack, which might reduce pressure on Iranian leadership to retaliate kinetically.
- There have also been incidents of misattribution that might be intentional: For instance, when major cyberattacks occur amid this conflict, sometimes other players are initially suspected. In 2020, when a huge explosion hit Iran’s Natanz facility, some experts wondered if it was a result of a US-Israeli cyber operation or an internal Iranian accident. Iran capitalized on that ambiguity in media to avoid admitting breach. Likewise, in 2021 when Israel’s Hillel Yaffe hospital was crippled by ransomware, it was attributed to a likely Russian criminal group, but Israeli analysts quietly assessed an Iranian link because no ransom negotiation was serious – hinting it was possibly a cover for a targeted Iranian wiper. These shadow games make attribution an intelligence challenge.
- Another dimension is “false flag” malware traces: Advanced attackers can plant code or use infrastructure to implicate a third party. Security researchers caution that both Israeli and Iranian APTs might deliberately reuse snippets from Chinese or Russian malware to throw off investigators. To date, most operations have been uncovered as Israeli or Iranian despite these tricks, but the potential to spark conflict by misdirecting blame is there. Imagine a scenario where Iran hacks Israel but makes it look like Russia did it – this could complicate Israel’s response (not wanting to confront Russia). Such scenarios worry policymakers, especially as the conflict intensifies and more groups get involved.
Funding and Laundering Operations
Cyber operations require funding – to pay hackers, buy infrastructure (servers, domains), and develop tools. How do Israel and Iran fund their cyber campaigns, especially Iran under sanctions? And how do they launder money or financially sustain proxy operations?
- State budgets and black budgets: Israel’s cyber ops are government-funded; Unit 8200 is part of the defense budget. Additionally, Israel’s intelligence agencies likely allocate black budget funds to cyber missions (e.g. using proceeds from secret tech exports). For Iran, the IRGC’s cyber command is funded by the state (IRGC has large revenue streams from businesses and smuggling too), but Iran’s economic woes mean they often have hackers find their own funding through crime. Iranian groups have stolen intellectual property that can be monetized (industrial designs, pharma data), and engaged in illicit fundraising – such as the ransomware and banking fraud noted. U.S. Treasury officials have traced how Iranian threat actors cash out Bitcoin via exchanges in Iran or Turkey, turning ransomware payments into usable funds for the IRGC.
- Cryptocurrency flows: Crypto has enabled Iranian actors to bypass the formal banking system. After major hacks or ransom incidents, there’s often a surge of crypto movement associated with Iranian wallets. For example, after the 2021 gas stations attack, there were unverified reports that some Iranian Bitcoin accounts swelled – possibly rewards from the state to the hackers or payments for zero-day exploits purchased. On the Israeli side, to fund covert ops, they might use crypto to pay foreign assets or hackers quietly. Israel also keeps a watch on crypto to track Iranian illicit finance (as with Nobitex hack, likely to gather account info of IRGC dealings in crypto).
- Laundering and fronts: Both sides use front companies to procure cyber tools or infrastructure. Iran has front companies in Malaysia, Turkey, and elsewhere that buy software/hardware which might be restricted under sanctions (like surveillance gear or exploits) and then covertly supply Iran. Payments for these might be laundered via Dubai businesses or through complex trades (oil-for-tech swaps). Israel, needing less covert procurement, still uses companies to disguise operations – for example, Israeli intel might set up a fake tech firm to approach and recruit a hacker from abroad, paying them through that shell.
In essence, a clandestine financial network underpins many of these cyber operations, making full accountability hard. As one analysis noted, crypto and the dark web have become part and parcel of the Iran-Israel cyber struggle, with crypto wallets serving as both a piggybank for hackers and a target for enemy hackers, and dark web forums acting as both arms bazaar and battleground.
Patterns of False Flags and Misattribution
To illustrate how tangled this can get: In 2022, a cyberattack hit an Israeli university. A group calling itself “Anonymous Sudan” claimed credit, but later it was revealed to be likely an Iranian operation using a Sudanese persona (Sudan being an Iranian ally historically). Similarly, when Iranian hackers hit U.S. voter databases in 2020, they sent emails pretending to be American far-right extremists. And in mid-2025, during the height of conflict, some pro-Iranian hacktivists defaced Israeli websites with messages attributed to a fictional Jewish anarchist group – a bizarre double-bluff attempt to sow internal Israeli discord.
The use of false flags can sometimes be uncovered by skilled threat intelligence (by analyzing code, infrastructure overlaps, linguistic tells). For example, Check Point noted that although Iranian groups try to disguise their work, they often reuse certain servers or tools, so they get unmasked. Nonetheless, the confusion sown can delay responses and hamper deterrence; each side can probe boundaries without immediately triggering an all-out response if blame isn’t clear.
In conclusion, third parties and proxies make the Israel-Iran cyber war a shadowy, many-layered conflict. It’s not just two monolithic states dueling – it’s a swarm of hacker groups, some genuine, some puppets; it’s mercenaries and criminals exploited for strategic ends; it’s online propaganda armies on social media amplifying hacks for psychological effect. This complicates attribution and raises the possibility of mistakes – e.g., punishing the wrong actor. It also enables escalation under the radar; a state might feel emboldened to strike via a proxy, thinking it won’t be caught and thus won’t escalate to a shooting war. But as these webs of deniability grow, so does the risk of miscalculation.
The international community, therefore, faces a conundrum: how to rein in these proxy cyber wars. Norms against using non-state hackers or against attacking civilian infrastructure exist on paper (like the UN norms of responsible state behavior), but Iran and Israel operate in a gray zone outside of formal agreements. Until there is accountability – such as sanctions on states for proxy attacks, or global cybercrime crackdowns – we can expect this covert utilization of third parties to continue or even intensify.
Civilian Impact and Collateral Damage: How Cyber Sabotage Affects Populations and Stability
Cyber warfare between states is often discussed in technical or strategic terms, but it’s crucial to assess its real-world impact on everyday people, economies, and regional stability. In the case of Israel and Iran, what began as covert operations on military targets has increasingly expanded to affect civilian infrastructure. This section examines the consequences of these cyber-sabotage operations on civilian populations and the broader economy, and how both governments and societies are responding. We also explore the ripple effects on regional/global stability – could these cyber conflicts spill over or escalate into something bigger?
Impact on Civilians and Critical Services
Numerous incidents illustrate that civilians are not just incidental victims but sometimes direct targets in the Israel-Iran cyber conflict:
- Public Utilities and Health: The attempted water system poisoning in Israel (April 2020) stands out as a stark example of an attack explicitly endangering civilians. Had Israeli cyber defenses not caught the anomaly in time, hundreds of families might have ingested toxic water or lost water access in the middle of a heatwave. This would have been a public health crisis, possibly the first known case of cyber warfare causing mass illness. Similarly, Iran’s retaliatory focus on civilian petrol stations in 2021 and 2023 meant ordinary Iranians sat in gas lines for days, unable to buy fuel. In October 2021’s incident, frustrated citizens saw digital pump screens displaying the taunting question, “Where is the fuel?” with a hotline number linked to the Supreme Leader’s office – a psychological ploy that sowed confusion and anger at the regime. The immediate effect was public chaos and outrage, demonstrating how cyber strikes can undermine trust in authorities. Moreover, when hospitals are targeted – as with the Iran/Hezbollah hack of Israel’s Hadera hospital (Nov 2023) or the attempted hit on Boston Children’s Hospital – it puts lives at risk. In the Safed hospital case, Israeli officials said the attack “aimed to disrupt the hospital’s regular operations” including potentially life-saving treatments. Even though it was thwarted, some sensitive patient data was stolen and later leaked, violating patient privacy and potentially compromising care. We’ve also seen Iranian hackers go after medical research institutes and pharmaceutical supply chains in the West, which could indirectly harm patients by delaying drug development.
- Economic Disruption: Many of these cyber operations have economic fallout. The May 2020 hack on Iran’s shipping port caused backups that cost companies money in delays and perishable goods spoilage. The fuel system attacks not only inconvenienced drivers but also hurt small businesses relying on fuel transport and likely cost the government millions in lost sales during the outage. For Israel, attacks on companies – like the 2020-21 waves of ransomware/wiper hits on insurance firms, banks, and the Tel Aviv light rail project – led to financial losses, downtime, and expensive recovery efforts. The CEO of one targeted Israeli insurance firm (Shirbit) described the aftermath of a breach as “a nightmare of system restoration and customer distrust”. Even if no lives are lost, the economic damage from sustained cyber campaigns can erode a country’s GDP growth and divert substantial resources to cybersecurity and remediation. A statistic from late 2023: Israel’s Cyber Directorate noted 800 cyber incidents with significant damage potential in 2023, many aimed at “destabilizing essential organizations and influential companies within supply chains”. This indicates a deliberate strategy to shake economic stability – for instance, hitting an IT provider whose services many businesses depend on (to create cascade effects).
- Psychological Impact and Public Morale: Beyond physical or economic harm, there is a psychological dimension. Constant cyber threats create a climate of fear and uncertainty among civilians. Iranians have experienced unexplained explosions and infrastructure failures that many suspect are foreign sabotage – this can cause public paranoia or rally anti-Israel sentiment. On the Israeli side, knowing that an adversary tried to poison your water or could try to hack your emergency services undermines the sense of security. After the water attacks, Israeli newspapers ran headlines asking if the country was prepared for a “cyber 9/11” and officials publicly warned that “cyber winter is coming”, which, while intended to prompt vigilance, also spread alarm. Additionally, the leakage of personal data (like the Black Shadow hacks releasing details of LGBTQ Israelis) had a chilling effect – some victims feared harassment or blackmail once their info was online. Cyber propaganda (e.g. hijacking TV broadcasts in Iran to show anti-regime slogans) can also cause psychological stress and confusion.
- Essential Services Reliability: Frequent low-level cyber assaults (website defacements, minor database leaks) may not individually be devastating, but over time they can degrade trust in institutions. If citizens regularly hear that their hospitals, power utilities, or financial institutions have been breached, they might lose confidence in those services. In Iran, repeated hacks have led to a mindset among some citizens that “our infrastructure is porous and our government can’t protect us.” This erodes regime credibility. In Israel, a country that prides itself on tech prowess, successful hacks by Iran (even small ones) are seen as a blow to national pride and can cause public outcry demanding better cyber defenses.
Importantly, both governments, while trying to shield their populations, have also used these incidents for political narrative. Israel’s leadership often emphasizes that Iran’s readiness to attack civilian targets like water or hospitals proves the unethical, dangerous nature of the Iranian regime, thereby justifying strong retaliatory stances. Iran’s regime, when its civilians suffer (like gas lines), tends to blame Israel and the U.S. loudly, attempting to channel public anger toward external enemies rather than at its own failings. Thus, civilian-impacting cyberattacks become propaganda tools for both sides – which can further inflame tensions.
Adaptation: Government and Private Sector Responses
As the threat to civilians and economies has grown, so too have efforts to defend against it:
- Israel’s measures: Israel has been proactive in bolstering cyber defenses. In 2016, it established the National Cyber Directorate as a centralized body to secure critical infrastructure and coordinate responses. This agency works closely with the IDF’s Cyber Defense Unit and Shin Bet (internal security) to monitor networks 24/7, share threat intelligence with private companies, and simulate attack scenarios. For instance, after the 2020 water attack wake-up call, the Cyber Directorate ordered immediate audits and basic fixes (like password changes and removing online access points) across water facilities. They also rolled out a nationwide early-warning system for critical utilities – analogous to a “cyber radar” – aiming to detect anomalous traffic that might indicate a cyber intrusion (some of this technology was reportedly provided by private Israeli startups). Israel conducts regular national cyber drills, often war-gaming simultaneous cyber and rocket attacks to test resilience. One such drill in 2021, “Omega”, simulated a scenario of widespread power outages caused by cyber attacks during a conflict, and helped expose gaps now being addressed (like backup generator coordination and public communication strategies during cyber-induced blackouts).The Israeli private sector, being highly tech-driven, has also stepped up. Banks in Israel have formed an information-sharing forum to alert each other and the government at the first sign of cyber anomalies – credited with quickly identifying the Pay2Key ransomware wave in 2020 and limiting its spread. Israeli utility companies have increased their cybersecurity budgets significantly, employing specialist firms (often run by ex-8200 personnel) to do “red team” tests on their systems. Additionally, Israel launched a program to bring in ethical hackers (“white hats”) to probe municipal systems for weaknesses before enemies do, a kind of crowdsourced defense. Culturally, there is a push to raise public awareness: campaigns telling people to practice good cyber hygiene (e.g. not clicking unknown links, using 2FA) because one careless user can let in a nation-state attacker.
- Iran’s measures: Iran, after being hit repeatedly, has taken measures albeit with more limited resources. Post-Stuxnet, Iran created a Cyber Defense Command under its Civil Defense Organization to work on protective tools (some Iranian experts developed their own anti-malware after foreign antivirus companies were suspected of collusion). Iran has heavily segmented its sensitive networks – for instance, nuclear facilities and oil terminals have been cut off from the internet (“air-gapped”) as much as possible. When Iran feared cyber infiltration in 2019, it even isolated the entire country from the global Internet temporarily, testing a domestic intranet called “National Information Network”. This points to a strategy of cyber isolation for protection. Of course, disconnecting services has economic costs and isn’t feasible long-term for everything, but Iran has shown willingness – e.g., after the 2022 Albania incident (which Iran carried out), Albania severed ties and Iran perhaps learned how a retaliatory strike might hurt them if roles were reversed.In terms of building resilience, Iran has tried to develop indigenous versions of foreign software so that it isn’t reliant on potentially compromised Western tech. For example, they have domestic industrial control software for some plants now, and their own banking transaction system for internal use to avoid SWIFT. The IRGC has also reportedly invested in backup communication networks (even radio-based) for its forces in case conventional networks get taken down by cyber means. After the petrol station hack, Iran’s authorities were criticized for not having a manual override – since pumps stopped working when the central smart card system failed. In response, they have implemented manual backup modes (and as of 2023, are testing a more decentralized fuel authorization system, so one hack can’t paralyze all stations). Iran also passed new cyber laws to penalize any insiders aiding attacks and to require critical sectors to implement cybersecurity standards (though enforcement is uneven). A major challenge for Iran is attracting and retaining top cyber talent for defense – many skilled Iranian techies emigrated or prefer lucrative offense roles. The Iranian government has thus started offering more perks to “cyber soldiers” on defense, framing it as patriotic duty.
- International cooperation and private aid: Interestingly, despite being adversaries, both Israel and Iran have at times received or offered quiet assistance from third parties to mitigate civilian harm. For instance, when Iran’s hospitals were hit by ransomware (likely by criminals) in 2021, security researchers from Europe provided decryption keys and Iran thanked them publicly, an unusual cross-border goodwill gesture. Similarly, when Israeli hospitals saw increased targeting in late 2023, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) shared threat intelligence with Israel given the common Iranian origin of threats. This underscores that cyberattacks on civilians can spur international solidarity, as no one wants to see patients or ordinary people suffer.
- Adapting military strategy: Both nations have begun factoring cyber heavily into their military doctrines. Israel’s concept of “cyber iron dome” has been floated – an integrated system to intercept cyber threats just as Iron Dome intercepts rockets. While not a physical dome, it means layered defense where critical systems are heavily monitored and can automatically isolate at the first sign of intrusion. Iran, noting its relative weakness, has embraced the idea of “cyber asymmetric warfare” – attacking soft targets in retaliation for kinetic blows. Iran’s military planners openly talk about using cyber to hit an enemy’s home front (water, electricity) since they can’t match Israel plane-for-plane. This means the civilian impact is not a side effect but rather part of Iran’s deterrence strategy. Recognizing this, Israeli defense planning now treats major cyber attacks on civilian infrastructure as events that could trigger conventional retaliation, trying to establish a deterrence of its own: essentially signaling to Iran that a cyber attack causing significant civilian harm is tantamount to a physical attack and will be met forcefully. Whether this message has been fully received is unclear, but it reflects adaptation to protect civilians.
Regional and Global Stability
The continual cyber sparring between Israel and Iran has implications far beyond their borders:
- Risk of wider conflict: Cyberattacks could accidentally trigger wider war. Imagine a cyber attack causes an explosion in a chemical plant that kills civilians – the victim state might retaliate militarily. In 2019, there were genuine fears that after Iran shot down a U.S. drone and the U.S. responded with a cyber strike, Iran might lash out at Israel or Gulf states’ infrastructure, spiraling escalation. Each time a major cyber incident occurs, other countries brace for fallout. In late 2023, as Israel-Iran tensions flared alongside the Israel-Hamas war, the U.S. government issued warnings that Iran could target U.S. companies or infrastructure in retaliation. This kind of advisory (shields up, etc.) is becoming standard whenever things heat up in the Middle East, illustrating how Iran-Israel cyber conflict threatens global networks and can entangle other nations.
- Spillover to allies: Iranian hackers have hit Saudi Arabia, the UAE, European universities, American cities – often as part of the same campaigns targeting Israel. Likewise, Israeli-linked cyber operations (like Stuxnet) involved U.S. resources and also infected systems in other countries unintentionally. The 2022 Albania hack by Iran (retribution for MEK’s presence) led to Albania cutting diplomatic ties with Iran – a direct diplomatic fallout of a cyber operation. That in turn saw NATO formally condemn Iran’s actions, raising geopolitical temperatures. If, say, Iranian hackers aiming at an Israeli target accidentally take down part of a European power grid (a plausible scenario via collateral damage), it could trigger EU involvement and elevate the confrontation. Already we have observed U.S. and European agencies openly calling out Iranian operations (sanctioning individuals, etc.), effectively siding with Israel’s position that Iran is the aggressor in cyber space. Conversely, Iranian allies like Hezbollah and perhaps even Russia (diplomatically) might rally if Israel were blamed for a particularly egregious cyber act on Iran. This proxy dynamic means the conflict exerts pressure on international cyber norms and alliances.
- Normative erosion: The repeated targeting of civilian infrastructure by both sides flouts the emerging international norms that urge states to refrain from such attacks during peacetime. For instance, the 2015 UN GGE report(which Iran and Israel aren’t exactly champions of, but still) included a norm against harming critical infrastructure that provides services to the public. Iran’s cyber strike on Albanian government services in 2022 was explicitly called out by the White House as violating peacetime norms about protecting the public. Each incident that goes without a strong international response arguably weakens the taboo against these kinds of operations. The danger is other states may look at Israel and Iran and conclude that power grids, hospitals, and water systems are fair game if you have a justified grievance. There is no cyber “Geneva Convention” with teeth yet, so this shadow war might be setting a de facto precedent that critical civilian infrastructure can be weaponized as long as it’s done covertly enough.
- Global cyber arms race: Observers note that the Israel-Iran rivalry has led both to sharpen their cyber swords, which in turn spurs others to do the same. Israel’s success with Stuxnet inspired nations like North Korea to develop destructive cyber capabilities. Iran’s ability to retaliate digitally provides a playbook for weaker states to deter stronger foes asymmetrically. We see more countries investing in offensive cyber units, often with an eye on “doing what Iran did” to punch above weight. This can destabilize regions beyond the Middle East; for example, Iran reportedly shared some cyber know-how with allies like Syria’s government and even Venezuela. An unstable equilibrium emerges where more states are tempted to carry out sabotage covertly rather than face opponents in open warfare, potentially leading to more frequent cyber incidents globally.
- Civil society and human rights: On a societal level, the constant cyber conflict has side effects on freedom and governance. In Iran, government justification of cyber defense has at times been used to justify tighter internet controls and censorship – e.g. citing the need to secure the country, they crack down on VPNs and force data localization, which also helps quash dissent. In Israel, the heightened cyber focus leads to extensive surveillance measures to preempt attacks, raising debates on privacy. The involvement of private Israeli firms (like NSO Group) in selling powerful spyware has drawn criticism that tools originally meant for fighting terror (or Iran) ended up being misused by authoritarian regimes – a byproduct of the robust cyber industry Israel built partly due to the Iran threat. Thus, the conflict indirectly has impacted digital rights worldwide (as seen in the Pegasus spyware scandals).
Despite these concerns, there is also a positive angle: the stark reality of this cyber shadow war has alerted many governments and companies to urgently improve their cyber defenses. The phrase “Cyber Pearl Harbor” has been used in think-tanks for years, and the Israel-Iran case provides concrete scenarios of what that might look like. For instance, the U.S. accelerating its pipeline cybersecurity regulations in 2022 was partly motivated by observing what Iranian actors might attempt (given they already hit water systems). Countries worldwide are now more aware that critical infrastructure needs strong cyber safeguards, and that deterrence in cyber is tricky so defense is essential.
In summary, the impact of Israel-Iran cyber hostilities on civilians is significant and multifaceted: direct disruption of daily life, psychological stress, economic costs, and even health and safety risks. Both nations are actively fortifying their defenses and adapting strategies to protect their people, but the threat is far from eliminated. Globally, this shadow war acts as both a cautionary tale and, unfortunately, a possible harbinger of how future conflicts could unfold in cyberspace – with civilians firmly on the frontline.
Implications for International Cyber Norms and Future Conflicts
The prolonged and shadowy cyber conflict between Israel and Iran is not happening in isolation – it is shaping, and being shaped by, the broader context of international cyber norms (the unofficial “rules of the road” for state behavior in cyberspace). It also offers lessons for global powers and smaller states alike on how cyber tools may be used in future conflicts. In this section, we explore what this confrontation means for the evolving norms of cyber warfare and what insights can be drawn for preventing or managing similar conflicts.
Erosion or Evolution of Norms?
At present, the norms around state-sponsored cyber operations are still nascent. There have been multilateral efforts (UN Groups of Governmental Experts, the Open-Ended Working Group, etc.) that articulate voluntary norms like “do not attack critical infrastructure providing services to the public” and “avoid malicious ICT activity that intentionally damages critical infrastructure”. The Israel-Iran case demonstrates blatant violations of these norms by both parties – essentially calling into question the effectiveness of such norms in the face of high-stakes security interests:
- Civilian Infrastructure as Fair Game: As detailed, both sides have targeted civilian infrastructure (power, water, hospitals, transport) outside of any formally declared war. This undercuts the normative stance that such targets are off-limits in peacetime. The fact that there have been minimal international consequences (e.g., no UN sanctions specifically for the water attack or fuel attack) might embolden other countries to consider doing the same. It sets a dangerous precedent: if Israel and Iran can engage in these tactics without being censured beyond statements, others may quietly prepare to replicate them against their adversaries.
- Ambiguity and Attribution Norms: One norm floated internationally is that states should not conduct or knowingly support ICT activity that harms other states’ critical infrastructure. Iran and Israel both officially deny involvement in many of these attacks, exploiting the inherent ambiguity of cyberspace. This highlights a gap in norms: without clear attribution, norms enforcement is stymied. Both states have mastered the art of “plausible deniability” in cyber operations, which essentially dilutes the power of norms since one can always deflect blame. The international community still lacks a reliable mechanism for neutral attribution that could call out bad behavior in a way that galvanizes action.
- Retaliation and proportionality: Traditional laws of war insist on proportional response and minimizing civilian harm. In cyber exchanges, we see a sort of unwritten tit-for-tat understanding evolving – e.g., Iran hits Israel’s water; Israel responds to Iran’s port. There seems to be a tacit “equivalence” being recognized (water vs. port, data theft vs. data theft). However, this is perilous because misjudging proportionality in cyber (which effect is worse?) could lead to escalation. The Israel-Iran dynamic might be fostering a new norm of reciprocal covert retaliation, as opposed to escalation to overt conflict. In a sense, they’ve treated cyber attacks as a separate domain where they can strike each other without it automatically triggering missiles and bombs. This compartmentalization could be seen as a norm in itself (“keep it in cyber, don’t let it spill over”). If that holds, it might prevent war – but if either side breaks that rule (like if a cyberattack causes deaths and then kinetic war erupts), it will set a severe counter-example.
- The norm of non-interference: International norms also say don’t interfere in other states’ internal affairs via cyber (like election meddling, etc.). Iran has meddled in Israel’s (leaking info on officials, psychological operations) and the US’s elections. Israel has meddled in Iran’s internal stability (hacking TV stations to show anti-regime content, leaking information to embarrass leaders). This suggests both consider such interference acceptable tools. It weakens the norm against cyber-enabled influence operations. The global worry is, if every adversary starts hacking each other’s politics, it could greatly destabilize international relations and trust in democratic processes.
Shaping Future Conflicts
Looking ahead, the Israel-Iran cyber conflict offers several lessons or harbingers for future state conflicts:
- Cyber as a Parallel Battleground: It’s clear now that any future conflict between sophisticated states (or even states and non-state actors) will have a concurrent cyber dimension. Israel and Iran have essentially been at war in cyberspace even when not in open kinetic war. This model – a persistent low-intensity cyberwar running in parallel to diplomatic tensions or proxy wars – is likely to be emulated elsewhere. For instance, we already see echoes in the US-Russia and US-China relations, where constant cyber espionage and occasional sabotage occur without open conflict. The key difference is Israel and Iran have been more public with the destructive element. So militaries worldwide are reorganizing to treat cyber operations as co-equal with land, sea, air, space. The concept of a “cyber first strike” is now very real: one could imagine future wars beginning with a wave of cyberattacks to blind and paralyze the adversary, as Israel perhaps envisages doing to Iran’s air defenses, or Iran dreams of doing to U.S. bases via hacking.
- The problem of escalation control: One sobering lesson is how unpredictable the feedback loop can be. Cyber exchanges can escalate or de-escalate in weird ways. Israel and Iran have occasionally shown restraint – for example, Israel did not respond to the Boston Children’s Hospital Iranian hack with an immediate similar strike, perhaps calculating it was better to quietly thwart it and not escalate involving U.S. civilian targets. But at other times, seemingly small cyber events triggered bigger responses (the water hack leading to a cascade of infrastructure attacks that summer). This indicates that escalation control in cyberspace is difficult because there’s no established communication or treaties specifically for cyberattacks. Unlike nuclear arms, there’s no hotline for cyber incidents between foes. One misinterpreted cyber event could lead to real war if seen as a major attack. Thus, a lesson is the need for confidence-building measures: e.g., agreements to refrain from targeting certain critical sectors, or at least to signal intentions (some propose a Geneva-like accord to not attack hospitals with cyber weapons – something Iran flagrantly violated). Future conflicts might force states to come to the table to hash out at least minimal cyber rules (perhaps after a severe incident scares everyone enough).
- Defense and resilience are paramount: A clear takeaway is that even offensive juggernauts like Israel can be hurt if they neglect defense. This conflict has underscored to all nations that critical infrastructure must be reinforced. Countries around the world have been investing in things like backup systems, incident response teams, and cybersecurity standards for utilities. For example, after seeing Iran probe water systems, the U.S. EPA tried (albeit with legal hurdles) to mandate water facilities include cybersecurity in safety audits. NATO has been war-gaming scenarios similar to the Israel-Iran incidents, to ensure collective defense could handle a cyber sabotage event. Nations are discussing if a cyberattack on one (e.g., a power grid hack) could trigger a mutual defense pact like NATO’s Article 5 – a heavy question influenced by the kind of threats Iran and Israel are trading.
- Deterrence in cyber – new approaches: The Israel-Iran case shows classic deterrence (like nuclear deterrence) doesn’t map neatly to cyber. Israel’s superior capability hasn’t deterred Iran from attacking; Iran’s unpredictability hasn’t deterred Israel from striking. Instead, both sides seem undeterred, willing to take hits and respond in kind. This suggests deterrence in cyberspace might require different tools – maybe more focus on entanglement (making systems so interconnected that attacking hurts oneself too) or stronger international legal punishment for crossing certain lines. Alternatively, some scholars suggest that establishing credible cyber retaliation options (like publicly demonstrating you can take out the other’s grid, as a warning) might deter more effectively. Israel might be inching toward this by leaking bits about its capabilities, and Iran by openly discussing how they’d hack back in event of war. How future conflicts play out will inform whether a strategy of deterrence by punishment can work in cyber, or if deterrence by denial (just make yourself very hard to hack) is the only reliable path.
- Role of international law and organizations: So far, neither Israel nor Iran has gone to the UN or international court specifically over cyberattacks (they have over physical incidents). This indicates the international legal system is not yet equipped or trusted to deal with cyber conflict. Going forward, there may be pushes to update the Laws of Armed Conflict to explicitly cover cyber sabotage (e.g., define when a cyberattack constitutes an “armed attack” under Article 51 of the UN Charter). The Israel-Iran saga could be a case study in a future cyber Geneva convention debate. For now, it’s in a legal grey zone – which arguably encourages more aggression because neither feels bound by clear legal consequences.
- Lessons for smaller states and non-aligned countries: Countries not directly involved can learn from Israel and Iran’s experience. One lesson: invest in cybersecurity now, because even regional conflicts can spill over and target your infrastructure (e.g., Iranian malware accidentally hitting European servers). Another: build alliances and information-sharing – Israel has benefited from Western intel, and Iran from perhaps Russian tacit support. Those outside might consider joining cooperative cyber defense groups (like the NATO CCDCOE) or regional CERT coalitions to not face threats alone. Also, smaller states are watching how effective cyber operations are compared to conventional ones. If, say, Iran manages to significantly blunt Israel’s military actions via cyber in a future clash, other countries facing powerful militaries might up their cyber game as a cost-effective equalizer. On the flip side, if Israel continues to stymie Iran’s nuclear program via cyber sabotage without firing a shot, it sets a precedent that cyber can achieve strategic goals quietly – something great powers have already noted and acted on (the U.S. reportedly used cyber operations to hinder North Korea’s missile program similarly).
In conclusion, the Israel-Iran cyber rivalry is charting new territory in state conflict, for better or worse. It has highlighted the urgency of establishing norms and agreements to avoid catastrophic outcomes, yet also shown how difficult that is when core interests are at stake and attribution is muddy. It is shaping military doctrines worldwide, proving that cyber tools are now integral to conflict and can have strategic effects akin to traditional weapons.
The implications are that we are entering an era where nations must expect and prepare for persistent, clandestine cyber aggression as part of the geopolitical landscape. International norms will likely lag reality, but eventually, perhaps through painful lessons, some consensus may emerge on lines that shouldn’t be crossed (maybe an eventual norm akin to “no cyberattacks on hospitals” could crystallize, given the universal abhorrence of such an act). The Israel-Iran shadow war might in hindsight be seen as the frontline where the “rules” of cyber warfare were forged – through trial by fire (or trial by code).
For global powers and vulnerable states today, the conflict underscores a few key lessons:
- Strengthen your defenses relentlessly, assume you are already penetrated, and practice responses.
- Engage in dialogue and norms discussions now – even if adversaries aren’t ready, laying groundwork is important so that if a crisis occurs, there’s a reference for behavior.
- Be cautious in offensive cyber use, as it can have unintended cascading effects and might break tacit boundaries that keep conflicts limited.
- Support international efforts to fight cybercrime and proxy hackers, since those proxies can be the foot soldiers of state cyber wars.
- Recognize cyber warfare’s impact on civilians, and incorporate humanitarian considerations into cyber strategy (something like the equivalent of not bombing civilians should apply in cyber too – a norm that needs reinforcement).
In essence, the Israel-Iran shadow cyberwar serves as both a warning and a guide. It warns how easily cyber operations can ratchet up and hit societies where it hurts, but it also guides us in what strategies might work (or not) in deterring and mitigating such conflicts. The world would do well to pay attention to this laboratory of cyber warfare in the Middle East, as its outcomes are likely to resonate far beyond, influencing how the next conflicts – wherever they are – will be fought or perhaps even prevented.
Conclusion and Recommendations
The shadow cyberwar between Israel and Iran over the past decade reveals a complex battlefield that is largely invisible yet has very tangible consequences. We have mapped out how this conflict has evolved – from the Stuxnet attack that opened Pandora’s box, to a relentless series of tit-for-tat hacks targeting nuclear facilities, water supplies, ports, hospitals, and more. Both nations’ elite cyber forces (Israel’s Unit 8200 and Iran’s IRGC Cyber Command) have expanded their capabilities and tactics in a high-stakes game of cat and mouse. They have planted malware landmines in each other’s critical systems, enlisted proxy hackers and criminal networks to do their bidding, and shown a willingness to put civilian infrastructure in the crosshairs. This ongoing covert war is shaping global cyber norms by violating them – highlighting the urgent need for clearer rules and stronger defenses to protect civilian life in the digital age.
Major Findings:
- Scale of Operations: The true frequency of Israel-Iran cyber attacks is far higher than publicly reported. What reaches headlines (like the Natanz explosions or nationwide gas station hacks) is just a fraction of continuous low-visibility operations including espionage, data theft, and foiled sabotage attempts. Many attacks remain unconfirmed officially, as secrecy and deniability cloak both sides’ actions. Nonetheless, leaks and cybersecurity forensic reports have exposed a pattern of persistent campaigns – not isolated incidents – essentially a constant cyber campaign just below the threshold of overt war.
- Targets and Impact: Initially focused on sensitive military projects (e.g. Iran’s nuclear program via Stuxnet), the cyber conflict has increasingly targeted civilian critical infrastructure. We documented incidents of Iranian hackers attempting to poison Israeli drinking water, and Israeli-linked malware shutting down 70% of Iran’s gas stations. These operations directly affect civilians: causing economic disruption, threatening health and safety, and sowing public fear. Hospitals have come under cyber-attack from Iran’s proxies (e.g. the thwarted hack on an Israeli hospital attributed to an IRGC/Hezbollah group), a particularly alarming trend that violates international norms of protecting medical services.
- Cyber Unit Evolutions: Israel’s Unit 8200 has solidified its reputation as a world-class cyber offense unit, integrating cutting-edge private-sector innovation and producing or procuring advanced cyber weapons (like zero-click phone spyware and sophisticated ICS malware). Its recruits are among the most talented youths, and its alumni fuel Israel’s high-tech boom. Iran’s IRGC Cyber Command, while initially behind, has dramatically improved – moving from simple website defacements to complex campaigns using custom malware, ransomware-as-cover, and clever social engineering. Iran’s cyber forces frequently operate via contracted hacker groups and proxies, enabling them to mount global operations despite economic constraints. Notably, both countries now regularly employ proxies/false flags (e.g. Iran’s “Cyber Avengers” and Israel’s “Predatory Sparrow”) to conduct attacks under deniable identities.
- Sleeper Threats: Evidence suggests each side has likely pre-positioned malicious footholds in the other’s critical networks for potential future use. The Iranian exploit of Israeli-made PLCs in U.S. water systems and the Israeli ability to infiltrate Iranian industrial control software hint at this silent preparation. While exact backdoors remain classified, both sides act as if the other could crash parts of their infrastructure in a conflict’s first moments. This has led to increased defensive postures: Israel hardening and isolating key systems, and Iran building redundancies and even an isolated national intranet to limit damage. The risk of these sleeper cells is a major security concern globally – raising questions of deterrence (are such covert implants equivalent to an act of war?) and emergency response (are we prepared if they activate?).
- Third-Party Role: The conflict is not just bilateral – other states and non-state actors play roles. The U.S. has been indirectly involved (both as a partner to Israel in ops like Stuxnet and as a target of Iranian cyber retaliation). Cybercriminal gangs and dark web marketplaces have been tapped to launder money or procure exploits, blurring lines between state action and organized crime. The use of cryptocurrencies by Iranian hackers to fund operations (and Israeli hackers to exfiltrate funds from Iranian targets) is notable. Also, Iran’s coordination with groups like Hezbollah brings a hybrid cyber-terror element into play. This makes attribution harder and raises the risk of misdirected blame or escalation via proxies.
- Global Stability and Norms: The Israel-Iran cyber war underscores the inadequacy of current international norms. Attacks on civilian infrastructure during peacetime – supposedly off-limits – have occurred, and there has been little accountability beyond diplomatic finger-wagging. This sets a worrying precedent that such behavior is becoming normalized. Furthermore, other nations are learning from this conflict, potentially spurring a cyber arms race as they observe that cyber tools can achieve strategic effects without the costs of conventional war. The conflict also highlights how easily cyber hostilities can entangle others (e.g., NATO ally Albania suffering an Iranian cyberattack, or U.S. hospitals being targeted when Iran is provoked).
Given these findings, we present the following recommendations tailored to different stakeholders:
For Policymakers (National and International):
- Establish Clear Red Lines and Communication Channels: It is imperative to define what actions are intolerable in cyberspace and communicate them explicitly to adversaries. For example, nations should declare that cyberattacks causing mass civilian harm (e.g. disabling hospitals, water poisoning) are red lines that could prompt severe responses. Back-channel or direct crisis communication mechanisms between rivals (akin to the Cold War “hotline”) should be set up for cyber incidents, to prevent misinterpretation and uncontrollable escalation. The Israel-Iran case shows the danger of ambiguity; having a way to quickly clarify “was that you?” could avert a shooting war started by a cyber misunderstanding.
- Pursue Cyber Norms with Teeth: Diplomatic efforts at the UN and other forums must continue, but with a focus on practical measures. Countries should push to formalize norms protecting civilian infrastructure – perhaps even a binding treaty – and create consequences for breaching them. One proposal is to form a coalition of states that pledge not to target certain critical services and agree to collective sanctions on those who do. This could start with like-minded states and gradually bring in others by setting an example. While getting Israel and Iran to agree now may be unrealistic, broad international consensus increases pressure and isolates norm violators. Additionally, supporting initiatives for independent cyber attribution organizations (to investigate major incidents) would help pierce the deniability that Iran and others exploit.
- Engage in Middleman Diplomacy: Even if Israel and Iran won’t talk directly, international mediators (neutral countries or organizations) should quietly facilitate norms dialogue. For instance, track-two dialogues involving retired cyber officials from each side, moderated by a neutral party, could explore boundaries (e.g., maybe both sides can agree not to hit hospitals, as a starting confidence-building measure). Successful communication here could later be scaled up. Also, leverage influence of allies: countries like Russia or China, which have ties to Iran, and the US/EU, which have sway with Israel, might encourage restraint in specific areas if it aligns with their interests (e.g., urging Iran not to hit financial networks that could cause global instability).
- Prepare Legal and Proportional Response Frameworks: Policymakers should develop legal doctrines for when a cyberattack constitutes an act of war and merits self-defense under international law. Clarity in this area can itself deter adversaries. If Iran knows a certain cyberattack will invite a kinetic Israeli strike (and international support for Israel’s response), it might think twice. Conversely, outline what proportional cyber retaliation looks like to avoid uncontrolled spirals. This conflict has largely been kept in the shadows; having doctrine on proportionality (perhaps using damage-based criteria) might help keep responses measured and focused on ending the conflict rather than escalating it.
For Cybersecurity Professionals and Critical Infrastructure Operators:
- Harden Critical Systems and Practice Incident Response: The Israel-Iran experience is a wake-up call to assume your infrastructure will be targeted by state-level threats. Professionals should implement robust network segmentation, up-to-date patching (especially of any Israeli or Iranian-made software which we’ve seen being targeted), 24/7 monitoring with anomaly detection (AI-driven if possible), and stringent access controls (zero-trust principles). Conduct regular red team/blue team exercises simulating the kind of attacks seen in this conflict: ICS malware infiltration, ransomware scenarios, etc. For example, simulate a coordinated attack on your power SCADA system and practice how to isolate it and switch to manual mode safely. The time to debug your disaster recovery plans is before a nation-state is trying to plunge you into darkness.
- Information Sharing and Threat Intelligence: Establish or join industry ISACs/ISAOs (Information Sharing and Analysis Centers/Organizations) for your sector to share threat intelligence in real-time. Israel’s companies benefited from quickly sharing indicators during the Pay2Key and MuddyWater attacks, enabling collective defense. Make sure to incorporate IoCs (Indicators of Compromise) from known Iran-Israel operations – many reports (from CISA, NSA, Check Point, etc.) have published indicators like file hashes, phishing domains, and malware signatures. Your security teams should actively ingest these and hunt in your networks. Partner with national CERTs and even international ones – cybersecurity has a strong community across borders that can sometimes bypass political noise to help each other in crises.
- Drill the “What-If” Scenarios: Professionals in utilities, hospitals, finance, etc. should ask: What if tomorrow we are hit with a Stuxnet-like attack or a massive data wipe? Develop specific playbooks: how to safely shut down operations to contain damage, how to communicate with the public if services are disrupted (to prevent panic), and how to coordinate with law enforcement/government bodies. The difference between chaos and order in a cyber crisis often comes down to preparedness. For instance, have offline backups and a means to restore critical systems if networks are compromised. Ensure you can reach key personnel and stakeholders if email and phones are down (satellite phones or out-of-band comms). Israel’s quick restoration of port operations in 2020, and Iran’s eventual recovery of fuel distribution in 2021, likely owe to having contingency plans – learn from those who went through it.
- Focus on Operational Technology (OT) Security: Many Iranian attacks exploited the weakest links in OT (like default passwords on PLCs). If you operate industrial controls, invest in OT-specific security solutions that monitor control commands and can flag anomalous or unsafe operations (like a sudden command to increase chlorine injection in water treatment). Network intrusion detection for OT networks, unidirectional gateways (data diodes) where feasible, and rigorous change management for any control logic can thwart attackers or at least give early warning before they cause damage.
For Civil Society and the General Public:
- Awareness and Digital Hygiene: An informed public is a harder target. Civilians should understand that in today’s world, cyberattacks can and do affect daily life – from gas pumps to hospital appointments. Basic cyber hygiene (strong, unique passwords, skepticism toward unsolicited emails/messages, using security updates) by individuals can help reduce the success of broad phishing campaigns that often precede major attacks. For example, an Iranian phishing campaign targeting Israeli researchers might start with a simple malicious email; if people are vigilant and report such attempts, the attack can be disarmed early. Governments and NGOs should run public awareness campaigns akin to “see something, say something” but for cyber threats.
- Demand Accountability and Transparency: Civil society should press their governments to be transparent (to the extent possible) about cyber incidents and what is being done to prevent them. Secrecy often surrounds these issues, but citizens have a right to know when their water or healthcare systems were put at risk and what lessons were learned. Holding leaders accountable ensures that there is political will to invest in cyber defenses and to pursue diplomatic solutions. For instance, after the water facility hack, Israeli media scrutiny helped spur faster hardening of infrastructure. In Iran, public outcry over the gas station chaos put pressure on officials to improve cyber readiness and not downplay issues. Public opinion can also push governments toward restraint: if citizens voice that attacking hospitals is unacceptable, it may influence policymakers to avoid or condemn such actions.
- Support International Cyber Peace Initiatives: Civil society organizations, universities, and think tanks across countries can collaborate on cyber peace efforts – for example, track and call out cyberattacks on civilians, advocate for international norms, facilitate dialogues. There are already projects visualizing cyber incidents globally; expanding these to explicitly cover civilian-impact incidents could raise awareness. When incidents do happen, independent investigations (by cybersecurity experts, perhaps with journalistic partnerships) can sometimes provide honest attribution and expose the truth even if governments won’t – this can reduce the chance of false flag deception and help the public know who is accountable. Essentially, civil society can serve as a watchdog and truth-teller in the fog of cyberwar.
- Personal Preparedness: Just as people keep supplies for natural disasters, having some personal preparedness for cyber-induced disruptions is wise. Keep printed copies of critical information (bank contacts, medical records) in case digital systems go down. Have some cash on hand if ATMs or payment systems fail temporarily (Iranians experienced this during certain outages). Know basic safety steps – for example, if there’s a widespread power outage (possibly cyber-caused), treat intersections as four-way stops, etc. These are general disaster tips but applicable here. The goal is not to be alarmist, but realistically, the more the public is prepared and stays calm during infrastructure incidents, the less the attacking side achieves its aim of panic and chaos.
In closing, the Israel-Iran cyber conflict is a stark illustration of how 21st-century warfare is extending into our digital and civilian realms. It is a call to action for governments, industries, and communities around the world. The shadow war need not continue in perpetuity; through diligent defense, smart diplomacy, and international cooperation, its worst potentials can be mitigated. Yet, we must be clear-eyed: as long as fundamental geopolitical disputes persist between determined adversaries, cyber weapons will be among the tools they wield.
The task ahead is to prevent this shadow war from escalating into a major catastrophe, and to build norms and safeguards such that cyberspace can become less of a wild frontier. The Israel-Iran saga – fraught with sabotage and subterfuge – ultimately underlines a paradox: our infrastructures and societies are deeply vulnerable, yet through resilience and collective effort we can blunt the impact. By learning from this conflict’s lessons, the international community can strive to ensure that the digital domain is used to connect and improve lives, rather than as a silent battleground undermining the very fabric of modern civilization.




Comments ()